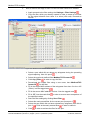
Download Real-Time Ethernet Kit Analysis Examples
Transcript
User Manual Real-Time Ethernet Kit Analysis Examples Hilscher Gesellschaft für Systemautomation mbH www.hilscher.com DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public Introduction 2/128 Table of Contents 1 INTRODUCTION.........................................................................................................4 1.1 About the User Manual ...............................................................................................4 1.1.1 1.1.2 1.1.3 1.2 Legal Notes.................................................................................................................7 1.2.1 1.2.2 1.2.3 1.2.4 1.2.5 2 Methods of Measurement .........................................................................................10 Overview of Measuring Examples ............................................................................10 CONDITIONS FOR PERFORMING THE MEASUREMENTS...................................11 3.1 3.2 3.3 Hardware and Software Installation..........................................................................11 Capture of the Data Frames .....................................................................................11 Arranging netANALYZER .........................................................................................12 3.3.1 3.4 Scaling with Sliders ............................................................................................14 Scaling with the Mouse ......................................................................................15 PROFINET IO ANALYSIS .........................................................................................16 4.1 4.2 Hardware Assembly..................................................................................................16 Preparing and Performing the Time Measurement...................................................17 4.2.1 4.2.2 4.2.3 4.2.4 4.2.5 4.3 4.4 Preparing Time Measurement............................................................................17 Adjusting Filter Settings......................................................................................18 Determining Direction of Signal Flow .................................................................22 Settings in the Analysis Windows.......................................................................24 Performing Measurement...................................................................................25 Performing Data Capture..........................................................................................28 Performing a Network Load Analysis........................................................................33 4.4.1 4.4.2 4.4.3 5 Settings for Recording of Telegrams..................................................................13 Scaling in the Timing Analysis Window ....................................................................14 3.4.1 3.4.2 4 Copyright ..............................................................................................................7 Important Notes ....................................................................................................7 Exclusion of Liability .............................................................................................8 Warranty ...............................................................................................................8 Export Regulations ...............................................................................................9 METHODS OF MEASUREMENT AND EXAMPLES.................................................10 2.1 2.2 3 List of Revisions ...................................................................................................4 Conventions in this Manual ..................................................................................5 Further Information ...............................................................................................6 Preparing Network Load Analysis ......................................................................33 Adjusting Filter Settings......................................................................................34 Starting the Netload Analysis .............................................................................38 ETHERCAT ANALYSIS ............................................................................................41 5.1 5.2 Hardware Assembly..................................................................................................41 Preparing and Performing the Time Measurement...................................................42 5.2.1 5.2.2 5.2.3 5.2.4 Preparing Time Measurement............................................................................42 Adjusting Filter Settings......................................................................................43 Settings in the Timing Analysis Windows...........................................................44 Performing Measurement...................................................................................46 Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 Introduction 5.3 6 3/128 Performing Data Capture..........................................................................................52 ETHERNET/IP ANALYSIS ........................................................................................56 6.1 6.2 Hardware Assembly..................................................................................................56 Performing Data Capture..........................................................................................57 6.2.1 6.3 Preparing and Performing the Time Measurement...................................................62 6.3.1 6.3.2 6.3.3 6.3.4 6.4 6.5 Preparing Network Load Analysis ......................................................................78 Adjusting Filter Settings......................................................................................78 Performing the Netload Analysis ........................................................................81 SERCOS III ANALYSIS.............................................................................................84 7.1 7.2 Hardware Assembly..................................................................................................84 Preparing and Performing the Time Measurement...................................................85 7.2.1 7.2.2 7.2.3 7.2.4 7.3 8 Preparing Time Measurement............................................................................62 Adjusting Filter Settings......................................................................................63 Settings in the Timing Analysis Windows...........................................................68 Performinging the Measurements ......................................................................69 Performing Data Capture..........................................................................................74 Preparing and Performing a Network Load Analysis ................................................78 6.5.1 6.5.2 6.5.3 7 Determining Connection ID ................................................................................61 Preparing Time Measurement............................................................................85 Adjusting Filter Settings......................................................................................86 Settings in the Timing Analysis Windows...........................................................88 Performing the Measurements ...........................................................................90 Performing Data Capture..........................................................................................95 MODBUS/TCP ANALYSIS ........................................................................................99 8.1 8.2 Hardware Assembly..................................................................................................99 Preparing and Performing the Time Measurement.................................................100 8.2.1 8.2.2 8.2.3 8.2.4 8.3 8.4 Preparing Time Measurement..........................................................................100 Adjusting Filter Settings....................................................................................101 Settings in the Timing Analysis Windows.........................................................106 Performing the Measurements .........................................................................108 Performing Data Capture........................................................................................112 Preparing and Perform a Network Load Analysis ...................................................117 8.4.1 8.4.2 8.4.3 Preparing Network Load Analysis ....................................................................117 Adjusting Filter Settings....................................................................................117 Performing the Network Load Measurement ...................................................121 9 GLOSSARY.............................................................................................................124 10 APPENDIX ..............................................................................................................125 10.1 10.2 10.3 List of Figures .........................................................................................................125 List of Tables ..........................................................................................................127 Contacts..................................................................................................................128 Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 Introduction 1 4/128 Introduction 1.1 About the User Manual This user manual contains descriptions of measurement examples, which can be build up with the components of the Real-Time Ethernet Kit. 1.1.1 List of Revisions Index Date Chapter Revisions Index 2 2009-03-10 Real-TimeEthernet-Kit all Created. 3 2010-07-01 Real-TimeEthernet-Kit all Adaption to netANALYZER, software version 1.3.0.0 and to CIFX 50-RE Rev 3. 4 2012-11-19 Real-TimeEthernet-Kit all Adaption to netANALYZER, software version 1.4.x.x New functions: Netload analysis, history display. Table 1: List of Revisions Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 Introduction 1.1.2 5/128 Conventions in this Manual Operation instructions, a result of an operation step or notes are marked as follows: Operation Instructions: ! <instruction> or 1. <instruction> 2. <instruction> Results: " <result> Notes: Important: <important note> Note: <note> <note, where to find further information> Positions in Figures , , ... or , , ... or , , ... refer to the The Positions figure used in that section. If the numbers reference to a section outside the current section then a cross reference to that section and figure is indicated. Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 Introduction 1.1.3 6/128 Further Information In this document the following user manuals are referenced netANALYZER-Card PCI RTE - NANL-C500-RE, netANALYZER-Box PCIe RTE - NANL-B500E-RE, and netANALYZER-Software, SW Version 1.4.x cifX-Karten Real-Time-Ethernet NXIO 50-RE-Board User manual Real-Time Ethernet Kit: Communication systems for Real-Time Ethernet Installation, Operation and Configuration Note: The interconnection of the NXIO 50-RE boards as shown in the measurement examples is only permitted for laboratory conditions. Note: Take care of the remarks on the installation of wireshark in the netANALYZER User Manual Rev. 12, section 14.3. Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 Introduction 1.2 1.2.1 7/128 Legal Notes Copyright © Hilscher, 2008-2012, Hilscher Gesellschaft für Systemautomation mbH All rights reserved. The images, photographs and texts in the accompanying material (user manual, accompanying texts, documentation, etc.) are protected by German and international copyright law as well as international trade and protection provisions. You are not authorized to duplicate these in whole or in part using technical or mechanical methods (printing, photocopying or other methods), to manipulate or transfer using electronic systems without prior written consent. You are not permitted to make changes to copyright notices, markings, trademarks or ownership declarations. The included diagrams do not take the patent situation into account. The company names and product descriptions included in this document may be trademarks or brands of the respective owners and may be trademarked or patented. Any form of further use requires the explicit consent of the respective rights owner. 1.2.2 Important Notes The user manual, accompanying texts and the documentation were created for the use of the products by qualified experts, however, errors cannot be ruled out. For this reason, no guarantee can be made and neither juristic responsibility for erroneous information nor any liability can be assumed. Descriptions, accompanying texts and documentation included in the user manual do not present a guarantee nor any information about proper use as stipulated in the contract or a warranted feature. It cannot be ruled out that the user manual, the accompanying texts and the documentation do not correspond exactly to the described features, standards or other data of the delivered product. No warranty or guarantee regarding the correctness or accuracy of the information is assumed. We reserve the right to change our products and their specification as well as related user manuals, accompanying texts and documentation at all times and without advance notice, without obligation to report the change. Changes will be included in future manuals and do not constitute any obligations. There is no entitlement to revisions of delivered documents. The manual delivered with the product applies. Hilscher Gesellschaft für Systemautomation mbH is not liable under any circumstances for direct, indirect, incidental or follow-on damage or loss of earnings resulting from the use of the information contained in this publication. Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 Introduction 1.2.3 8/128 Exclusion of Liability The software was produced and tested with utmost care by Hilscher Gesellschaft für Systemautomation mbH and is made available as is. No warranty can be assumed for the performance and flawlessness of the software for all usage conditions and cases and for the results produced when utilized by the user. Liability for any damages that may result from the use of the hardware or software or related documents, is limited to cases of intent or grossly negligent violation of significant contractual obligations. Indemnity claims for the violation of significant contractual obligations are limited to damages that are foreseeable and typical for this type of contract. It is strictly prohibited to use the software in the following areas: • for military purposes or in weapon systems; • for the design, construction, maintenance or operation of nuclear facilities; • in air traffic control systems, air traffic or air traffic communication systems; • in life support systems; • in systems in which failures in the software could lead to personal injury or injuries leading to death. We inform you that the software was not developed for use in dangerous environments requiring fail-proof control mechanisms. Use of the software in such an environment occurs at your own risk. No liability is assumed for damages or losses due to unauthorized use. 1.2.4 Warranty Although the hardware and software was developed with utmost care and tested intensively, Hilscher Gesellschaft für Systemautomation mbH does not guarantee its suitability for any purpose not confirmed in writing. It cannot be guaranteed that the hardware and software will meet your requirements, that the use of the software operates without interruption and that the software is free of errors. No guarantee is made regarding infringements, violations of patents, rights of ownership or the freedom from interference by third parties. No additional guarantees or assurances are made regarding marketability, freedom of defect of title, integration or usability for certain purposes unless they are required in accordance with the law and cannot be limited. Warranty claims are limited to the right to claim rectification. Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 Introduction 1.2.5 9/128 Export Regulations The delivered product (including the technical data) is subject to export or import laws as well as the associated regulations of different counters, in particular those of Germany and the USA. The software may not be exported to countries where this is prohibited by the United States Export Administration Act and its additional provisions. You are obligated to comply with the regulations at your personal responsibility. We wish to inform you that you may require permission from state authorities to export, re-export or import the product. Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 Methods of Measurement and Examples 2 10/128 Methods of Measurement and Examples 2.1 Methods of Measurement All methods of measuring have a time resolution of 10 ns. Start time and duration of measurement can be controlled by external signals. Data Recording With data recording, it is possible to store every telegram in network segment into a file. The telegrams can be selected according to some particular criteria. Time Measurements By time measurements, it is also possible when which telegrams occur with which frequency, and how much time the telegrams need between to points in the network. Analysis of Network Load The network load analysis enables you to measure the network load of different protocols on the Ethernet line. This shows up, which telegram types occur when and cause which network load. The network load analysis thus allows to identify and visualize unusual events. In order to avoid erroneous measurements, take care of activating only one single port for the measurements and thus preventing double measurements. 2.2 Overview of Measuring Examples Protocol Type of measurement Measurement PROFINET IO Time measurement using a hardware filter Cycle time, time delay of telegram passing through an IO device. Recording of telegrams Telegram storage with a filter, data conversion for Wireshark. Network Load Start-up time of PROFINET with filter on particular PROFINET telegrams. Time measurement using a hardware filter Cycle time, time delay of telegram passing through a slave and propagation time through a ring. EtherCAT EtherNet/IP sercos Modbus/TCP Recording of telegrams Telegram storage with a filter, data conversion for Wireshark. Time measurement using a hardware filter Cycle time master, cycle time slave, propagation time master, propagation time slave. Recording of telegrams Telegram storage with a filter, data conversion for Wireshark. Network Load Start-up time of EtherNet/IP, ping as disturbance on the network. Time measurement using a hardware filter Propagation time through primary ring, ConClk cycle time at slave. Recording of telegrams Telegram storage with a filter, data conversion for Wireshark. Time measurement using a hardware filter Response time, propagation time, cycle time. Recording of telegrams Telegram storage with a filter, data conversion for Wireshark. Network Load Start-up time of network and ping. Table 2: Overview of Measuring Examples Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 Conditions for performing the Measurements 3 3.1 11/128 Conditions for performing the Measurements Hardware and Software Installation 1. The PC card cifX and associated software must be installed. Details for the application can be found in the PC card cifX user manual. 2. The netANALYZER hardware and associated software must be installed. Details for use of the netANALYZER software can be found in the netANALYZER user manual. Additional Documents Please refer especially to the User manual Real-Time Ethernet Kit Communication Systems for Real-Time Ethernet Installation, Operation and Configuration which is included in this kit. This document describes the hardware and software installation of the individual components (CIFX 50RE and NXIO 50-RE). The instructions described in it are preconditions for carrying out these measurements and data capturing. Details of the Freeware software e. g. Wireshark that is used here can be taken from the documentation of the corresponding product. 3.2 Capture of the Data Frames In order to show the captured data contents, it is necessary to install a network monitoring program that supports the WinPcap format such as Wireshark. Wireshark is "free software", it can be downloaded from the following Internet address: http://www.wireshark.org/ respectively http://www.wireshark.org/download.html. A special Hilscher Dissector is integrated in Wireshark. Note: GPIO events of the NANL-C500-RE card are decoded by Wireshark from Version 1.0.0. If the display in Wireshark does not appear as “Hilscher- netANALYZER-GPIO-Event” after a new installation, then the corresponding protocol must be enabled in Wireshark as a one-time occurrence. Note: In addition, a plug-in must be installed in Wireshark Versions before 1.7.1 which can be found on the netANALYZER DVD. For this purpose see also section 6.4 “Display and Settings in Wireshark“ of the netANALYZER user manual rev. 12. Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 Conditions for performing the Measurements 12/128 Note: If a .pcap file contains a netANALYZER Info Block and if this plugin is not or is incorrectly installed then Wireshark (Version number ≤ 1.6) could incorrectly interpret the additional data at the end of the frame and show an incorrect frame. In this case de-enable either the generation of the Info Block or, better yet, install the netANALYZER plug-in. An existing Info Block with a non-installed plug-in is recognized by the message “netANALYZER frame info block” at the end of the frame. In the following some measurement examples for various Real-Time Ethernet protocols are described. This represents only a small sample of the measurement possibilities of the netANALYZER in order to show the principles of the application. These measurement examples are built up with the CIFX 50-RE, NXIO 50RE and netANALYZER hardware components and the associated cables. 3.3 Arranging netANALYZER ! Start the netANALYZER software netANALYZER > netANALYZER. " The main window appears. with Start > Programs > Figure 1: netANALYZER Main Window Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 Conditions for performing the Measurements 3.3.1 13/128 Settings for Recording of Telegrams ! Select Settings > File Settings (see Figure 1). " The window for configuring the paths and the file names of the .hea files opens. Figure 2: netANALYZER File Settings Description Allowed range of values / Value Max. number of .hea-files Maximum number of *.hea files to be stored until capturing is interrupted. Standard file size: 1GB Ring-buffer mode If checked, the captured data will be stored within the ring buffer. If not checked, the captured data will be stored within a stack buffer (stack buffer mode). In this mode the capturing process is automatically finished if all *.hea files (i.e. the checked / not checked, Default: checked GUI element number of *.hea files specified under full. ) are Name of .heafiles Denomination for *.hea files. Path of .heafiles Path to be specified by the user, under which the netANALYZER driver should store the binary file (*.hea). OK The settings are stored and the window is closed. 1 .. 255 characters Table 3: Description File Settings In this window you decide how many files are stored for capturing at which location. In this context, please also read section 8.4 of the User Manual netANALYZER. Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 Conditions for performing the Measurements 3.4 3.4.1 14/128 Scaling in the Timing Analysis Window Scaling with Sliders There is the possibility to expand or compress the graphical representation of both time axes. This should have the highest importance for the X time axis within the history window. ! For manual scaling switch off the Auto Scale feature . Figure 3: Timing analysis, change scaling The time axis above. The slider displays the entire measuring time period within the figure allows changing the width of the displayed time period. The slider allows changing the position of the displayed time period relative to the entire measuring time period. This applies for the Y time axis accordingly: The width of the displayed time period is adjusted with slider and the position on the time bar with slider . The measured events can very easily move outside of the displayed area. By clicking Auto Scale the display area is moved over the events again. Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 Conditions for performing the Measurements 15/128 Within the histogram, the X axis can be switched between linear and logarithmic scaling by selecting entry Axis from the combo box and vice versa. All 3 axes of the figure above can be adjusted with Auto Scale in such a manner, that all measuring events are located within the display area. 3.4.2 Scaling with the Mouse You can zoom areas by holding the left mouse button pressed. Figure 4: Timing Analysis, scaling with the Mouse ! Switch off Auto Scale . ! Mark an area with the left mouse button being pressed either horizontally in window area A 1 or vertically in window area A 2. " After releasing the mouse button the area within both partial windows is zoomed. ! In order to return to the original display, switch on Auto Scale Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public again. © Hilscher, 2008-2012 PROFINET IO Analysis 4 16/128 PROFINET IO Analysis The following timing parameters are to be measured here as an example: • measuring the cycle time which the IO Controller uses to sends a frame to an IO Device, • measuring the time a frame running through Device 1 for the frame of the Controller to Device 2, • measuring the network load for PROFINET IO telegrams at network start-up and at “ping”. 4.1 Hardware Assembly The following hardware assembly is required for this measurement example. Figure 5: PROFINET IO Analysis, Hardware Assembly The MAC addresses that apply for the assembly are listed above the components. Please ensure that the respective MAC addresses are unique in the world. For this reason the devices in your measurement assembly have different MAC addresses. Note: The settings for the cifX card and the NXIO 50 board must be accomplished in accordance with section 6.2 of the User manual RealTime Ethernet Kit - Communication Systems for Real-Time Ethernet Installation, Operation and Configuration. Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 PROFINET IO Analysis 4.2 17/128 Preparing and Performing the Time Measurement Note: The cifX card and the NXIO boards offer auto-crossover functionality. For this reason interchanging the cable at the netANALYZER at TAP A (Port 0 and Port 1) as well as at TAP B (Port 2 and Port 3) is without meaning. Thus, also with the display of the analysis values of the Port designation 0/1 or 2/3 can be seen as interchangeable. Note: Only the immediately required settings for this measurement assembly of the netANALYZER are described here. Detailed information on the setting and display possibilities of the software can be found in the in the User Manual netANALYZER NANL-C500-RE. 4.2.1 Preparing Time Measurement It is intended to measure the cycle time of frames of the cifX card to Device 2 and the device propagation time from Device 1 for these frames. ! Start the netANALYZER software with Start > Programs > netANALYZER > netANALYZER. " The main window of the netANALYZER opens. Figure 6: netANALYZER Entry Screen The respective linkage status (as shown for ) is marked UP when the cabling (as described in section Hardware Assembly on page 16) has been completed and the communication between the cifX card and the NXIO board is running. You can see in line Filter whether there is any filter active on this input line. Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 PROFINET IO Analysis 4.2.2 18/128 Adjusting Filter Settings ! Select Settings > Filter Settings to adjust the following settings. " The filter window appears as follows: Figure 7: netANALYZER Filter Settings (1) In order to adjust the settings required for measurement, proceed as follows: Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 PROFINET IO Analysis 19/128 Figure 8: netANALYZER Filter Settings (2) ! Double click onto the menu entry Filters > User defined " The entry Blank appears. ! Select the line Blank ! Click Copy Filter " The new entry . using the left mouse button. . appears under the filter selection. ! Choose a new name for the filter to be created (here PN_F_A). ! Click at Enable Filter A . Target MAC Address ! to which the data Fill in the Target MAC Address of the device are sent into the first 6 bytes of the value line of the filter. Take care of filling in the addresses of the used devices. Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 PROFINET IO Analysis 20/128 Source MAC Address ! beginning Fill in the Source MAC Address of the data packets with byte 0x6 up to byte 0xB of the value line. Take care of filling in the addresses of the used devices. Filter mask ! Fill in „FF“ into the mask fields below target and source address in order to include every character of the target and source address into the comparison. ! Take care of the entry Accept, if Filter A matches being checked within the specified selection line in order to include only those data packets, for which the selection matches. ! Click at Select Filters . In order to make these filter settings effective for all ports click Apply . to All Ports ! Store the filter settings by clicking Save Filter ! Leave the filter settings by clicking OK . . Note: The MAC addresses have to be adapted to your devices for your measuring assembly. Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 PROFINET IO Analysis 21/128 " The main window of the netANALYZER opens: Figure 9: netANALYZER, Selection Timing Analysis ! Select Timing Analysis . Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 PROFINET IO Analysis 22/128 " In the foreground, the window for graphic presentation of the Timing Analysis opens: Figure 10: netANALYZER Measurement Window The timing analysis window is divided into 4 subwindows consisting of two parts, namely histogram and history. In the further discussion of this measuring set-up usually we concentrate on only one of these 4 subwindows. The size of the single subwindows can changed by dragging the point where the window division lines cross. It is also possible to display only the history window or only the histogram window. You can adjust this in the main window of the netANALYZER under Settings > Analysis Configuration. 4.2.3 Determining Direction of Signal Flow ! Click the main window of the netANALYZER: ! Click Start and then click Stop (this is now situated at the position of the Start) so that some frames can be displayed. This is necessary in order to determine on which Ports the analyzer board will detect the frames. " The main window should now look as follows: Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 PROFINET IO Analysis 23/128 Figure 11: netANALYZER Main Window after Measurement Cycle Under TAP A there is now be seen in the row Frames received OK under Port 0 or Port 1 a quantity greater than (here Port 0). This port is important for the settings in the Timing Analysis window and is denominated as active port TAP A in the following. Under TAP B there is now be seen in the row Frames received OK under Port 2 or Port 3 a quantity greater than (here Port 2).This port is important for the settings in the Timing Analysis window and is denominated as active port TAP B in the following. Note: Because of the Auto crossover functionality of the Ethernet PHYs of the devices, it is possible with a restart of the measurement assembly for the Ports 0 and 1 or 2 and 3 to be interchanged. ! Change to the Timing Analysis window. Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 PROFINET IO Analysis 4.2.4 4.2.4.1 24/128 Settings in the Analysis Windows Settings for Analysis Window A In order to measure the cycle time of the request telegrams at Device 2: ! Adjust the following settings in sub window A: Figure 12: netANALYZER Measurement Window Settings 1 In this row you can enter a name for the measurement . In From: select the active port TAP A (here Port 1) section Determining Direction of Signal Flow page 22). (as determined in In To: select the active port TAP A (here Port 1) (as determined in section Determining Direction of Signal Flow page 22). With this setting the cycle time (selected via the filter) of the frames is measured. At this port we have detected the telegrams directed to Device 2 within Figure 11. Here the scaling of the Y axis can be switched between linear and logarithmic scaling . is set. This causes the results Ensure that the time axis Auto Scale always to be displayed within the visible part of the window. 4.2.4.2 Adjust the Settings in Window B In this example, the propagation time of telegrams through Device 1 shall be measured. ! To do so, make the following settings: Figure 13: netANALYZER Measuring Window Settings 2 In this row you can enter a name for the measurement . In From: select the active port TAP A (here Port 1) section Determining Direction of Signal Flow page 22). (as determined in In To: select the active port TAP B (here Port 3) section Determining Direction of Signal Flow page 22). (as determined in Ensure that the time axis Auto Scale is set. So you assure that the results will always be displayed within the visible part of the window. Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 PROFINET IO Analysis 4.2.5 25/128 Performing Measurement ! Click into the main window of the netANALYZER. Figure 14: netANALYZER Main Window Start/Reset ! Click Reset . This deletes the previously displayed time data. ! On Start to start the analysis. " The former Start button now becomes the Stop button. The graphical display of measurement values can be observed instantaneously. In the example displayed here, an evaluation has been made over a time of approximately 30 minutes. In this way the following figures have been generated. ! Wait for the time in which you would like to evaluate frames. ! Click Stop. " You will now find the following information in the subwindow A of the Timing Analysis window. 4.2.5.1 Result of Measurement in Subwindow A Figure 15: netANALYZER PROFINET IO Cycle time Measurement, auto-scale ! Switch off Auto Scale in order to adjust the optimal scale and time period with the sliders in the partial displays. The number of analyzed frames (123066). Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 PROFINET IO Analysis 26/128 The minimum cycle time in ns (with separation into groups of thousands), followed by the deviation to the average time specified in %. The average cycle time in ns (with separation into groups of thousands). The maximum cycle time in ns (with separation into groups of thousands), followed by the deviation to the average time specified in %. The max. and min. time values 16,03 ms and 15,97 ms indicate extreme values. In figure „A 1“ (the histogram) you can realize, that most of the telegrams are located within a significantly more narrow time window between approx. 15,992 ms and 16,008 ms . Within the history window „A 2“ you can find the time frames where the rare (Scaling) and events with large deviations by shifting the sliders (Time frame). These are tagged here as and . 4.2.5.2 Result of Measurement in Subwindow B " In window B of the timing analysis window you can now find the following information: Figure 16: PROFINET IO, Device 1 Propagation time ! Switch off Auto Scale , in order to adjust optimal scaling and time frame with the sliders within the partial displays. The number of telegrams being analyzed amounts to 123067. The minimum cycle time in ns (with separation into groups of thousands), followed by the deviation to the average time specified in %, here 7,77 µs. The average propagation time in ns (with separation into groups of thousands), here 7,838 µs. Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 PROFINET IO Analysis 27/128 The maximum propagation time in ns (with separation into groups of thousands) and following percentage value of the average measured time (here 8,55 µs und 9,08 %). This percentage value of the deviation seems to be very high at first sight. to logarithmic representation, then you can However, if you switch axis see in figure „B 1“ that only very few telegrams cause this deviation. In the history display „B 2“ you can see by shifting the sliders (Scaling) and (Time frame), that these events all occur in a very short time period . By increasing the resolution of the time scale of the history display even more, you can also determine the absolute time of these events. Figure 17: PROFINET IO, Device 1 Propagation Time, History extremely scaled Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 PROFINET IO Analysis 4.3 28/128 Performing Data Capture Both the frames of the cifX card to Device 2 and the response frames from Device 2 to the cifX card are to be captured. Preconditions: • The hardware assembly as described in section Hardware Assembly on page 16 must have been set up, • the settings for the cifX card must have been made, • data exchange between the cifX card and the Devices must have been established. ! Start the netANALYZER software with Start > Programs > Hilscher GmbH > Hilscher netANALYZER. " The main window of the netANALYZER opens. Figure 18: Main Window for Telegram Recording The respective linkage status (as shown for ) is marked UP when the cabling (as described in section Hardware Assembly on page 16) has been completed and the communication between the cifX card and the NXIO boards is running. If the filter settings from the timing analysis are still active, this will be . Check the filter settings for correctness! tagged with the label ACTIVE ! Proceed from the main window of the program to the filter settings using the Settings > Filter Settings dialog. Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 PROFINET IO Analysis 29/128 " The filter window appears as follows: Figure 19: netANALYZER PROFINET IO Filter Settings ! Adjust the settings shown above: which you have already created ! Open the User defined filter setting during the timing analysis. ! Select the stored filter PN_F_A Measurement on page 17. ! Check the checkbox Select Filter as defined in section Preparing Time . ! Click Apply to All Ports . ! Verify, that this filter setting is really valid for each port. ! Leave the window with OK . " You are returned to the main window. Figure 20: Start Data Capture ! Ensure that Capture data is turned on. ! Start the capture with a click Start . " The Start button becomes the Stop button. ! Wait until a sufficient number of frames have been captured. ! Click Stop . Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 PROFINET IO Analysis 30/128 ! Click Convert . " The following window appears: Figure 21: pcap Conversion 1 The pcap conversion window consists of 2 columns: Window Area User Interface Element Path Button All filtered .hea files for this name or capture Description Path to be defined by the user from which the netANALYZER shall read the binary file (*.hea) for conversion. The settings, which are done here, have an effect to the next capture. The settings done at Settings > File Settings are changed with it. Selection button for the selection of the source directory of the .hea files. List of .hea files in the selected directory. Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 PROFINET IO Analysis 31/128 Window Area User Interface Element Description Path Path to be defined by the user where the netANALYZER software shall store the converted WinPcap file (*.pcap) Button File name .pcap files that will be generated Selection button for the selection of the target directory for storing the .pcap files Systematic file denomination for the .pcap files. The netANALYZER software additionally appends a running number for each file within the filename. Preview of generated .pcap files The name structure is as follows: File name from . consecutive number. Time information, consists of yyyymmddhhmmss (start of the capture of the hea file, if ckeck Append date/time to is set). If checked, date and time are added within the file name pcap file name Include FCS in .pcapfiles Checkbox whether the Ethernet checksum shall be included within the PCAP file or not (Some Wireshark dissectors do not support FCS.) Note: If Convert to extended .pcap file including additional frame information is checked, Include FCS in .pcap-file is grayed out as FCS is always converted into a .pcap file then. FCS = Frame Check Sequence (Ethernet checksum) Not selectable, if option Include corrupted frames in .pcap file Append netANALYZER information block (for Wireshark versions before 1.7.1 with additional plug in only) If this option is activated, then also erroneous frames will be included into the .pcap file. If it is deactivated, only correct telegrams will be stored in the .pcap file. This option requires the installation of the netANALYZER Wireshark plug-in for Wireshark versions < V1.7.1. Adds the netANALYZER info block to the .pcap file after the Ethernet frame. This supplies additional information for each single telegram such as time of receipt, receiving port or error information. Note: The .pcap file format with info block after the Ethernet frame is no longer supported by Wireshark versions ≥ 1.7.1. Not selectable if option Convert to extended .pcap file including additional frame information Convert Close is checked, however active. is checked. Note: If this item is checked, the extended .pcap file format generated by the netANALYZER software V1.4.x.x can only be opened in Wireshark versions beginning with V1.7.1. Beginning with netANALYZER software V1.4.x.x an extended .pcap file format can be generated. There the netANALYZER info block is stored in the 4 bytes prior to the Ethernet frame. Therefore, additional information for each single telegram such as time of receipt, receiving port or error information is available. Conversion of binary files into the WinPcap format is started. The window is closed without starting any conversion. ! Select the file to be converted in window area ! Add the necessary settings in window area . . ! Click Convert in order to convert the data into the .pcap file format. ! Open the file with Wireshark. " The following data will be displayed. Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 PROFINET IO Analysis 32/128 ! Double click on the converted file (here c:\Default_001.pcap), or start the Wireshark program and select the file with the File > Open path. " The Wireshark program displays the data as follows: Figure 22: PROFINET IO netANALYZER Wireshark Telegram Display According to the filter settings, only telegrams sent from the cifX card to Device 2 have been recorded. In this window area all the displayed individual frames will be listed individually. In the Port column you will see the Port number of the netANALYZER board in which the frame was captured. In this window area the data of the selected frame in the window you area is shown at the protocol level. In the row 2 of this window area will see the Port number of the netANALYZER board at which the frame was captured. In this window area the data of the selected frame is shown at the byte level. Note: In the figure above, the individual frames have been shown twice. The reason is in the assembly of the switching from Hardware Assembly on page 16 and the selected filter setting, as the netANALYZER captures the data at each TAP and the filtered frames pass through both Ports. Thus, also the propagation time through Device 1 can also be seen. Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 PROFINET IO Analysis 4.4 33/128 Performing a Network Load Analysis The network load caused by the cifX card shall be analyzed. Furthermore, the amount of PROFINET protocol packets compared to the amount of packets of other protocols shall be analyzed. Finally, the network start-up behavior shall be examined. The following requirements apply: • The hardware must have been set up according to the description within section Hardware Assembly on page 16, • The settings of the cifX card must have been adjusted already. 4.4.1 Preparing Network Load Analysis The filter criteria must be determined and adjusted subsequently. ! For a short time record data from a running PROFINET network. ! Have a look at a standard PROFINET telegram. " This data set should look like this: Figure 23. Standard PROFINET Data Set In the figure above, the relevant filter data from to are tagged. A Standard PROFINET protocol telegram. The virtual LAN identifier (0x8100). The PROFINET identifier (0x8892). The Frame ID tag (0x80 02) ! With the data above an Extended Software Filter shall be configured. Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 PROFINET IO Analysis 4.4.2 34/128 Adjusting Filter Settings ! Switch off hardware filter Figure 24: Switch off hardware filter Note: The selected hardware filters apply additionally to the Extended at Software Filter. Therefore uncheck either checkbox Enable Filter the Hardware-Filter or uncheck checkbox Select Filter . ! Adjust software filter. ! For the configuration of the Extended Software Filters proceed as follows: 1. In the netANALYZER main menu click at menu entry Settings > Extended Software Filter Settings. " The following configuration window is displayed: Figure 25: Create Extended Software Filter (1) 2. Create the filter entries. Proceed as follows: ! If the window area contains more than displayed in the figure above, then erase the entries by clicking Clear Tree . ! Open the selection menu below Add Filter Entry entry Add Byte Match Entry. ! The following configuration window is opened: Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public and select the © Hilscher, 2008-2012 PROFINET IO Analysis 35/128 Figure 26: Create Extended Software Filter (2) ! Here you can enter the filter data, that you have investigated within Figure 23 below the entry : In the figure above below the byte position (here 12:13; take care of byte counting beginning at „0“),below the data contents of this the comparison condition (here „=“). Then (here 81 00) and below click OK . " The Extended Software Filter should now look like: Figure 27: Extended Software Filter after 1. Entry Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 PROFINET IO Analysis 36/128 Proceed as follows for the PROFINET identification: ! Determine the information for entry Figure 23. (PROFINET identification) from of the filter display above and then add the entry ! Tag the entry as described already „Bytes [16:17] = 88 92“ with Add Filter Entry for entry . Note: This generates an AND relation of the filter condition. If you had tagged the entry Start of the figure above, then you would have related both entries with an OR relation. " Now your filter should look like this: Figure 28: Extended Software Filter after 2. Entry ! In order to display a curve within the Netload Analysis display, you have to add an identification entry. ! To do so, click the entry tagged with in the filter display above. Then click Add Identification Entry. ! In the opening window enter a name for identification purposes. Here the name „PROFINET” has been entered. Note: If other data sets not matching the filter conditions occur during analysis, these will be registered with the identification Other. " Then the filter window will look like: Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 PROFINET IO Analysis 37/128 Figure 29. Extended Software Filter after 3. Entry ! Store the filter settings for later applications by clicking Save Tree and leave the filter window by clicking OK. " You return back into the main window of netANALYZER. Note: If during the analysis of telegrams further types of telegrams are detected, the analysis will be extended by „Other“. Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 PROFINET IO Analysis 38/128 Adjust the following settings here: Figure 30: netANALYZER Main Window PROFINET Netload Analysis ! Check the checkbox at TAP A for Port 0 and Port 1 . This is necessary as it is not predictable over which port the communication will start due to the Auto Crossover feature of the Ethernet ports. ! If necessary, uncheck the checkboxes at TAP B the telegrams from being recorded twice. 4.4.3 , in order to prevent Starting the Netload Analysis ! Select Netload Analysis . " The Netload Analysis window opens. ! In order to evaluate also the frames not originating from PROFINET during connection establishment, open the Ethernet connection at CH 0 of Device 1 in Figure 5 to be able to close it again after starting the recording of the analysis. ! Select the main window of the netANALYZER. ! Here, click Start. " The recording of analysis data begins. ! Reconnect the cable at CH 0 of the Device. ! After some time, stop recording by clicking Stop in the main window of the netANALYZER. " In the Netload Analysis window you can see information similar to the following: Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 PROFINET IO Analysis 39/128 Figure 31: Netload Analysis for PROFINET Start-up Phase Line in window area corresponds to line in window area . Line in window area corresponds to line in window area . Besides the selection made within the filter settings automatically the rest of the analysis events which is not included by the selection conditions of the filter settings is displayed as Other within the graphical display. Within window area you can see the numerical values of the recording, Right-click onto a frame type in order to select within the context menu the color of the curve, the type of line and its thickness. By right-clicking at window area linear and logarithmic Y-Scaling. , you can switch for instance between If you follow the curve with the mouse in the window area values of the measurement for this second are displayed Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public , the numerical . © Hilscher, 2008-2012 PROFINET IO Analysis 40/128 Figure 32: Extended Software Filter with FrameID Using the following Extended Software filter setting which additionally filters for a specific FrameID you get the following analysis picture for the start-up phase of the PROFINET network. Figure 33: Netload Analysis for PROFINET Start-up Phase with FrameID 8002 Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 EtherCAT Analysis 5 41/128 EtherCAT Analysis The following timing parameters are to be measured here as an example: • measuring the cycle time which the Master uses to access a slave, • measuring the frame running time through Slave 1, • measuring the ring propagation time of the frames. 5.1 Hardware Assembly The following hardware assembly is required for this measurement example. Figure 34: EtherCAT Analysis, Hardware Assembly Important! It is important, that Ethernet connector CH0 of the cifX card is connected to Ethernet connector CH0 of the NXIO 50 Board. Note: The settings for the cifX card and the NXIO 50 board must be accomplished in accordance with Section 6.3 of the User manual RealTime Ethernet Kit - Communication Systems for Real-Time Ethernet Installation, Operation and Configuration. Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 EtherCAT Analysis 5.2 42/128 Preparing and Performing the Time Measurement Note: The cifX card and the NXIO boards offer auto-crossover functionality. For this reason an interchange of the cable at the netANALYZER at TAP A (Port 0 and Port 1) as well as at TAP B (Port 2 and Port 3) is without effect. Thus, also at the display of the analysis values of the Port designation 0/1 or 2/3 can be considered as interchangeable. Note: Here only the settings of the netANALYZER immediately required for this measurement assembly are described. Detailed information on the setting and capture possibilities of the software can be found in the User Manual netANALYZER. 5.2.1 Preparing Time Measurement It is desired to measure the cycle time of frames of the cifX card to Slave 1 and the device running time from Slave 1 as well as the ring propagation time. ! Start the netANALYZER software with Start > Programs > netANALYZER > netANALYZER. " The main window of the netANALYZER opens. Figure 35: netANALYZER Entry Screen The respective linkage status (as shown for ) is marked UP when the cabling (as described in section Hardware Assembly on page 41) has been completed and the communication between the cifX card and the NXIO boards is running. Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 EtherCAT Analysis 5.2.2 43/128 Adjusting Filter Settings ! Select Settings > Filter Settings to adjust the following settings. Figure 36: netANALYZER Filter Window ! Select Filters > EtherCAT > All EtherCAT frames ! Click Select Filter . . ! Click Apply to All Ports . ! Check whether the selected filter is really applied to all ports. ! Leave the filter settings by clicking OK . " You are returned to the netANALYZER main window. ! In the netANALYZER main window select Timing Analysis . " The window for graphic representation of the Timing Analysis opens in the foreground: Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 EtherCAT Analysis 44/128 Figure 37: netANALYZER Timing Analysis window The timing analysis window is divided into 4 subwindows consisting of two parts, namely histogram and history. In the further discussion of this measuring set-up usually we concentrate on only one of these 4 subwindows. The size of the single subwindows can changed by dragging the point where the window division lines cross. It is also possible to display only the history window or only the histogram window. You can adjust this in the main window of the netANALYZER under Settings > Analysis Configuration. 5.2.3 Settings in the Timing Analysis Windows At first, take care of Auto Scale being set. Figure 38: netANALYZER Timing-Auto-Scale In this way you ensure, that if telegrams are detected these are also visible as bars and are not outside of the window area. ! Adjust the From / To conditions for each partial window as follows: Note: At your test setup, the telegrams may run over the respective corresponding port due to the Auto-Crossover feature of the ports of the netANALYZER card. If necessary adapt the ports according to your setup! Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 EtherCAT Analysis 5.2.3.1 45/128 Settings for Analysis Subwindow A In order to measure the cycle time of the telegrams of the cifX card to slave 1. ! Adjust the following settings in sub window A: Figure 39: Timing Analysis Window A, EtherCAT Cycle Time ! In this row you can enter a name for the measurement. Enter Cycle time here. ! In FROM: select Port 0 . ! In To: select Port 0 . The network cycle time is measured with these settings. Here the scaling of the Y axis can be switched between linear and logarithmic . ! Ensure that the Auto Scale 5.2.3.2 time axis is set. Adjusting the following Settings in Subwindow B Measurement of Ring Propagation Time Figure 40: Timing Analysis Window B, EtherCAT Ring Propagation Time (1) ! In From: select Port 0 . ! In To: select Port 1 . This setting is used to measure the time between the arrival of the frame at Port 0 and the arrival at Port 1. This can be the ring propagation time or the cycle time minus the ring propagation time. This can only be interpreted after successful measurement (see also settings for window 3). This possible ambiguity is the result of the Auto crossover functionality of the cifX card and the NXIO boards. 5.2.3.3 Adjusting the following Settings in Subwindow C In order to measure the ring propagation time / cycle time: ! Make the following settings in window C. Figure 41: Timing Analysis Window C, EtherCAT Ring Propagation Time (2) ! In From: select Port 1 . ! In To: select Port 0 . This setting is used to measure the time between the arrival of the frame at Port 0 and the arrival at Port 1. This can be the ring Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 EtherCAT Analysis 46/128 propagation time or the cycle time minus the ring propagation time. This can only be interpreted after successful measurement (see also settings for window 2). This possible ambiguity is the result of the Auto crossover functionality of the cifX card and the NXIO boards. 5.2.3.4 Adjusting the following Settings in Subwindow D In order to measure the signal propagation time of slave 1: ! Make the following settings in window D: Figure 42: Timing Analysis Window, EtherCAT Ring Propagation Time (2) ! In the Start Port select Port 0 (or possibly Port 1). ! In the Stop Port select Port 2 (or possibly Port 3). The signal running time through Slave 1 is found with one of the two setting pairs, with the other setting a size of the cycle time is found. 5.2.4 Performing Measurement ! Click in the main window of the netANALYZER. Figure 43: netANALYZER Start/Stop Analysis ! Click Reset ! ! ! ! 5.2.4.1 . This deletes the previously displayed time data. Click Start to start the analysis. The Start button becomes the Stop button. Wait for the time during which you would like to evaluate the frames. Click Stop. Measurement Result Window A: Cycle Time If From- and Stop-Port are identical, always the cycle time will be measured independently from the direction (data path from master to the slaves or from slave to master). Within the data path from the slaves to the master, the jitter may be increased. ! You will now find the following information in window A of the Timing Analysis window. Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 EtherCAT Analysis 47/128 Figure 44: EtherCAT Timing Analysis Window A with measured Data In figure „A 1“ (the histogram), the distribution of the number of telegrams is displayed in dependence of the deviation of the cycle time. In the history window „A 2“ , the distribution of the number of telegrams is displayed in dependence of the time. At At you can see under: Denomination Meaning Value Min Time The minimum cycle time and the percental deviation to the average cycle time 0.99 µs Av Time The average cycle time of the telegrams 1000.001 µs Max Time The maximum cycle time and the percental deviation to the average propagation time 1008.170 µs Std. Deviation The standard deviation of the cycle time 1.717 µs you can see under: Denomination Meaning Value Samples The number of evaluated telegrams 197013 Below Range The number of telegrams below the displayed time period (Y axis). 0 Over Range The number of telegrams above the displayed time period (Y axis). 0 Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 EtherCAT Analysis 48/128 The average cycle time is therefore 1 ms. All further measurements that lie within the size range of the cycle time are measurements between to and for paths of the frame. These are usually no meaningful measurements. 5.2.4.2 Measurement Result Window B: Ring Propagation Time " You will now find the following information in window B of the Timing Analysis window. Figure 45: EtherCAT Timing Analysis Window B with measured Data In figure „B 1“ (the histogram), the distribution of the number of telegrams is displayed in dependence of the ring propagation time. In the history window „B 2“, the distribution of the number of telegrams is displayed in dependence of the time. At you can see under: Denomination Meaning Value Min Time The minimum cycle time and the percental deviation to the average cycle time 5.49 µs Av Time The average cycle time of the telegrams 5.557 µs Max Time The maximum cycle time and the percental deviation to the average propagation time 5.63 µs Std. Deviation The standard deviation of the cycle time 31 ns Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 EtherCAT Analysis 49/128 At you can see under: Denomination Meaning Value Samples The number of evaluated telegrams 197014 Below Range The number of telegrams below the displayed time period (Y axis). 0 Over Range The number of telegrams above the displayed time period (Y axis). 0 Here you can see that the average ring propagation time is approximately 5.5 µs. Note: Because of the Auto crossover functionality of the Ethernet PHYs of the EtherCAT devices, it is possible with a restart of the installation for the Ports 0 and 1 to be interchanged. Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 EtherCAT Analysis 5.2.4.3 50/128 Measurement Result Window C: Cycle Time - Ring Propagation Time " You will now find the following information in window C of the Timing Analysis window. Figure 46: EtherCAT Timing Analysis Window C with measured Data Here you can see that this is not a meaningful measurement as the found protocol sequence time lies within the range of the cycle time. From the measurement results in the windows 2 and 3 it can be seen that in this assembly the signals from the Master run through Port 0 in the netANALYZER. Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 EtherCAT Analysis 5.2.4.4 51/128 Measurement Result Window C: Telegram Propagation Time through Slave 1 " You will now find the following information in window D of the Timing Analysis window. Figure 47: EtherCAT Timing Analysis Window D with measured Data Here it can be seen that the frame running time was measured through Slave 1. The single strips are caused by the time resolution of the netANALYZER card amounting 10 ns. In figure „D 1“ (the histogram), the distribution of the number of telegrams is displayed in dependence of the deviation of the cycle time. In the history window „D 2“ , the distribution of the number of telegrams is displayed in dependence of the time. At At you can see under: Denomination Meaning Value Min Time The minimum cycle time and the percental deviation to the average cycle time 1.16 µs Av Time The average cycle time of the telegrams 1.189 µs Max Time The maximum cycle time and the percental deviation to the average propagation time 1.22 µs Std. Deviation The standard deviation of the cycle time 13 ns you can see under: Denomination Meaning Value Samples The number of evaluated telegrams 197014 Below Range The number of telegrams below the displayed time period (Y axis). 0 Over Range The number of telegrams above the displayed time period (Y axis). 0 Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 EtherCAT Analysis 5.3 52/128 Performing Data Capture The frames of the cifX card to the Slaves and the response frames from the Slaves to the cifX card are to be captured. Preconditions: • The hardware assembly as described in section Hardware Assembly on page 41 must have been created. • The settings for the cifX card must be carried out. • A data exchange between the cifX card and the Slaves must exist. • The basic settings for the netANALYZER must be carried out as described in section Preparing Time Measurement on page 17. ! Start the netANALYZER software with Start > Programs > Hilscher > netANALYZER > netANALYZER. " The main window of the netANALYZER opens. Figure 48: EtherCAT netANALYZER Main Window The respective linkage status (as shown for ) is marked UP when the cabling (as described in section Hardware Assembly on page 41) has been built up and the communication between the cifX card and the NXIO boards is running then. Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 EtherCAT Analysis 53/128 ! Ensure that the filter is set up according to section Preparing Time Measurement as described at page 42 of this document. ! Click OK. " You are returned to the main window. Figure 49: Start Data Capture ! Ensure that Capture data is turned on. ! Start the capture with a click Start . " The Start button becomes the Stop button. ! Wait until a sufficient number of frames have been captured. ! Click Stop . ! Click Convert . " The following window appears: Figure 50: pcap Conversion 1 The pcap conversion window consists of 2 columns: Window Area User Interface Element Path Button All filtered .hea files for this name or capture Description Path to be defined by the user from which the netANALYZER shall read the binary file (*.hea) for conversion. The settings, which are done here, have an effect to the next capture. The settings done at Settings > File Settings are changed with it. Selection button for the selection of the source directory of the .hea files. List of .hea files in the selected directory. Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 EtherCAT Analysis 54/128 Window Area User Interface Element Description Path Path to be defined by the user where the netANALYZER software shall store the converted WinPcap file (*.pcap) Button File name .pcap files that will be generated Selection button for the selection of the target directory for storing the .pcap files Systematic file denomination for the .pcap files. The netANALYZER software additionally appends a running number for each file within the filename. Preview of generated .pcap files The name structure is as follows: File name from . consecutive number. Time information, consists of yyyymmddhhmmss (start of the capture of the hea file, if ckeck Append date/time to is set). If checked, date and time are added within the file name pcap file name Include FCS in .pcapfiles Checkbox whether the Ethernet checksum shall be included within the PCAP file or not (Some Wireshark dissectors do not support FCS.) Note: If Convert to extended .pcap file including additional frame information is checked, Include FCS in .pcap-file is grayed out as FCS is always converted into a .pcap file then. FCS = Frame Check Sequence (Ethernet checksum) Not selectable, if option Include corrupted frames in .pcap file Append netANALYZER information block (for Wireshark versions before 1.7.1 with additional plug in only) If this option is activated, then also erroneous frames will be included into the .pcap file. If it is deactivated, only correct telegrams will be stored in the .pcap file. This option requires the installation of the netANALYZER Wireshark plug-in for Wireshark versions < V1.7.1. Adds the netANALYZER info block to the .pcap file after the Ethernet frame. This supplies additional information for each single telegram such as time of receipt, receiving port or error information. Note: The .pcap file format with info block after the Ethernet frame is no longer supported by Wireshark versions ≥ 1.7.1. Not selectable if option Convert to extended .pcap file including additional frame information Convert Close is checked, however active. is checked. Note: If this item is checked, the extended .pcap file format generated by the netANALYZER software V1.4.x.x can only be opened in Wireshark versions beginning with V1.7.1. Beginning with netANALYZER software V1.4.x.x an extended .pcap file format can be generated. There the netANALYZER info block is stored in the 4 bytes prior to the Ethernet frame. Therefore, additional information for each single telegram such as time of receipt, receiving port or error information is available. Conversion of binary files into the WinPcap format is started. The window is closed without starting any conversion. ! Select the file to be converted in window area ! Add the necessary settings in window area . . ! Click Convert in order to convert the data into the .pcap file format. ! Open the file with Wireshark. " The following data will be displayed. Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 EtherCAT Analysis 55/128 ! Double click on the converted file (here c:\Default_001.pcap), or start the Wireshark program and select File > Open. The Wireshark program displays the data as follows: Figure 51: EtherCAT netANALYZER Wireshark Telegram Display This window area shows a list of all frames. In this window area you can see individual frame regions of the selected frame. In this window area the data of the selected frame is shown at the Byte level. Here a complete frame cycle of the measurement assembly is highlighted. The first row contains the frame as it comes from the Master. This was captured at Port 0. The second row contains the frame after the first Slave on the way to Slaves 2 and 3. This was captured at Port 2. The third row contains the frame as it returns from Slave 2, after it was already processed by Slave 3. This was captured at Port 3. The fourth row contains the frame as it is returned from Slave 1 to the Master. This was captured at Port 1. Here the part of the frame (third row of the cycle) is highlighted that contains the nominal values at the Slave. Here the part of the frame (third row of the cycle) is highlighted that contains the actual values from the Slave. Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 EtherNet/IP Analysis 6 56/128 EtherNet/IP Analysis The following timing parameters are to be measured here as an example: • measuring the answer cycle from Slave 3, • measuring the cycle time of the access of Slave 3, • measuring the propagation time through Slaves 1 and 2 in both signal directions. 6.1 Hardware Assembly The following hardware assembly is required for this measurement example. Figure 52: EtherNet/IP Analysis, Hardware Assembly The MAC addresses that apply for the assembly are listed above the components. Please note that the respective MAC addresses are unique in the world. For this reason the devices in your measurement assembly have different MAC addresses. Note: The settings for the cifX card and the NXIO 50 board must be accomplished in accordance with section 6.4 of the User manual RealTime Ethernet Kit - Communication Systems for Real-Time Ethernet Installation, Operation and Configuration. Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 EtherNet/IP Analysis 6.2 57/128 Performing Data Capture The connection ID of slave 3 for cyclic data transmission has to be determined. You need this information for the correct filter settings if you want to determine propagation times of slave telegrams with the timing analysis. ! In order to register all telegrams, all filters need to be switched off. To do so, proceed as follows: ! Stop any running data capture. ! In the main window of the netANALYZER select Settings > Filters Settings. " The window for filter settings opens: Figure 53: EtherNet/IP Filter Data Capture ! Select Port 0 . ! Select under User Defined Blank ! Check checkbox Select Filter . . ! Make these settings valid for all ports by clicking Apply to All Ports ! Click OK . . Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 EtherNet/IP Analysis 58/128 Figure 54: EtherNet/IP Data Capture Start ! Take care of all ports being selected for data capturing ! Select Capture Data . . ! Start capturing by clicking Start . " Data capturing begins, the start button turns to a stop button. ! Wait until some telegrams have been recorded. ! Click Stop and then click Convert to convert the data into the pcap format for the analysis with Wireshark. " The following window opens: Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 EtherNet/IP Analysis 59/128 Figure 55: Ethernet/IP netANALYZER Analysis Conversion 1 The window above is subdivided into two areas: Window Area User Interface Element Path Button All filtered .hea files for . Description Path to be defined by the user from which the netANALYZER shall read the binary file (*.hea) for conversion The settings, which are done here, have an effect to the next capture. The settings done at Settings > File Settings are changed with it. Selection button for the selection of the source directory of the .hea files List of .hea files in the selected directory this name or capture Window Area . User Interface Element Description Path Path to be defined by the user where the netANALYZER software shall store the converted WinPcap file (*.pcap) Button File name .pcap files that will be generated Selection button for the selection of the target directory for storing the .pcap files Systematic file denomination for the .pcap files. The netANALYZER software additionally appends a running number for each file within the filename. Preview of generated .pcap files The name structure is as follows: File name from . consecutive number. Time information, consists of yyyymmddhhmmss (start of the capture of the hea file, if ckeck Append date/time to is set). If checked, date and time are added within the file name pcap file name Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 EtherNet/IP Analysis Include FCS in .pcapfiles 60/128 Checkbox whether the Ethernet checksum shall be included within the PCAP file or not (Some Wireshark dissectors do not support FCS.) Note: If Convert to extended .pcap file including additional frame information is checked, Include FCS in .pcap-file is grayed out as FCS is always converted into a .pcap file then. FCS = Frame Check Sequence (Ethernet checksum) Not selectable if option Include corrupted frames in .pcap file Append netANALYZER information block (for Wireshark versions before 1.7.1 with additional plug in only) If this option is activated, then also erroneous frames will be included into the .pcap file. If it is deactivated, only correct telegrams will be stored in the .pcap file. This option requires the installation of the netANALYZER Wireshark plug-in for Wireshark versions < V1.7.1. Adds the netANALYZER info block to the .pcap file after the Ethernet frame. This supplies additional information for each single telegram such as time of receipt, receiving port or error information. Note: The .pcap file format with info block after the Ethernet frame is no longer supported by Wireshark versions ≥ 1.7.1. Not selectable if option Convert to extended .pcap file including additional frame information Convert Close is checked. is checked. Note: If this item is checked, the extended .pcap file format generated by the netANALYZER software V1.4.x.x can only be opened in Wireshark versions beginning with V1.7.1. Beginning with netANALYZER software V1.4.x.x an extended .pcap file format can be generated. There the netANALYZER info block is stored in the 4 bytes prior to the Ethernet frame. Therefore, additional information for each single telegram such as time of receipt, receiving port or error information is available. Conversion of binary files into the WinPcap format is started. The window is closed without starting any conversion. ! Select the file to be converted in window area ! Add the necessary settings in window area . . ! Click Convert in order to convert the data into the .pcap file format. " The window closes after the conversion was completed. ! Open the file with Wireshark. A double click on the .pcap file opens Wireshark, if the Wireshark program is installed correctly. " The following data will be displayed: Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 EtherNet/IP Analysis 6.2.1 61/128 Determining Connection ID Figure 56: EtherNet/IP Data Capture ! Select a telegram in window area to be cyclically sent by slave 3. ! Identify and tag the data set Connection ID in window area . this data set is displayed with the data position within " In window area This information is required for the filter settings to be applied if you want to determine propagation times of slave telegrams with the timing analysis Important: Do not interrupt the data communication in the measuring setup as with a restart of the data communication, the „Connection ID“ will be changed. Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 EtherNet/IP Analysis 6.3 62/128 Preparing and Performing the Time Measurement Note: The cifX card and the NXIO boards offer auto-crossover functionality. For this reason an interchange of the cable at the netANALYZER at TAP A (Port 0 and Port 1) as well as at TAP B (Port 2 and Port 3) is without meaning. Thus, also with the display of the analysis values of the Port designation 0/1 or 2/3 can be seen as interchangeable. Note: Here only the settings of the netANALYZER immediately required for this measurement assembly are described. Detailed information on the setting and capture possibilities of the software can be found in the User Manual netANALYZER NANL-C500-RE. As the Ethernet/IP slave sends its input data cyclically to a broadcast address on its own, in this case it is necessary to determine the Connection ID for the cyclic protocols of the slave prior to the measurement This Connection ID can be determined by a data recording, see section Performing Data Capture at page 57 and section Determining Connection ID at page 61. Note: The Connection ID is determined again at every network start-up. 6.3.1 Preparing Time Measurement In this example the times of the frame sequence from the cifX card (Master) to the NXIO board Slave 3 and return are to be measured. It is possible to analyze both signal directions in one common measurement. ! The MAC address of the cifX card must be determined. If the MAC address is not known, it can be determined as follows: Link the PC Ethernet network connection with the Ethernet connection of the cifX card. Start the “Ethernet Device Configuration” with Start > Programs > SYCON.net System Configurator > Ethernet-device setup. Enable the Search for device in the main window of the program. You will recognize the cifX card at the Ethernet/IP Scanner device type. ! You can determine the MAC addresses of the NXIO Board according to the description within section “EtherNet/IP” of document „User Manual Real-Time-Ethernet-Kit“. ! Start the netANALYZER software with Start > Programs > netANALYZER > netANALYZER. Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 EtherNet/IP Analysis 63/128 " The main window of the netANALYZER opens. Figure 57: EtherNet/IP netANALYZER Entry Screen If you have set up the cabling (as described within section Hardware Assembly on page 56) and the communication between the cifX card and the NXIO boards is running, the respective connection status (as displayed at ) is signed with UP with data rate or at elder netANALYZER boards at TAP B only with UP. 6.3.2 Adjusting Filter Settings ! Go to the main window of the program using the Settings dialog in the filter settings. " The filter window appears as follows: Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public Settings > Filter © Hilscher, 2008-2012 EtherNet/IP Analysis 64/128 Figure 58: EtherNet/IP netANALYZER Filter cifX # Slave 3 At first select an identical filter for all ports. Here the communication direction cifX to Slave 3 has been selected. ! Select Filters > Ethernet/IP > Cyclic frames . ! Copy this filter by clicking Copy Filter . ! Denominate the filter using a new name (here Cyclic frames to Slave ) for the filter. 3 ! Check Enable Filter A . Target MAC Address ! Fill in the target MAC address into the tagged area (i.e. the MAC ). address of Slave 3 Source MAC Address ! Fill in the MAC address of the cifX card into the tagged area. Note: For your measurement assembly the MAC addresses have to be adapted to your devices. Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 EtherNet/IP Analysis 65/128 Filter Mask into the Mask fields below source and target address in ! Fill in „FF“ order to ensure comparing every character within target and source address. ! Select Accept, if filter A matches . ! Select this filter for Port 0 by checking option Select Filters the mouse. ! Click Apply to All Ports at all ports. using in order to make this filter setting effective ! Store the filter settings by clicking Save Filter . Now during a measurement at all ports of the netANALYZER card the cyclic telegrams from the cifX card to Slave 3 are selected. All other telegrams will be filtered, i.e. rejected. ! Leave the filter settings by clicking OK 6.3.2.1 . Allocating Port Signal Flow Note: Because of the Auto crossover functionality of the devices, the Ports 0 and 1 as well as Ports 2 and 3 may be interchanged in your measurement assembly! ! Start the measurement for a short time. " In the netANALYZER Entry Window you will then get a display similar to the following one:. Figure 59: EtherNet/IP netANALYZER Direction of Signal Flow In the red boxes and in line Frames received OK below Port 1 and Port 3 you can find out that telegrams from the cifX to Slave 3 have been detected at those ports. Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 EtherNet/IP Analysis 66/128 Therefore it can be concluded, that the telegrams from Slave 3 to the cifX card run over Port 2 and Port 0 of the netANALYZER card. Note: Due to the Auto crossover functionality of the components the signals may run over Port 0 and 2 at your assembly. For these ports the filters are required to be set accordingly. 6.3.2.2 Createing Filter for Signal Direction from Slave 3 to the cifX As the slave sends to a broadcast address on its own, we can only work with the MAC source address and a connection ID. ! Proceed from the main window of the program to the filter settings via Settings > Filter Settings . " The dialog window for filter settings is opened where you perform the following settings: Figure 60: EtherNet/IP netANALYZER Filter Slave 3 # cifX ! Choose the pane for the desired port (on which no telegrams have been detected up to now), for which you want to create a new filter. (Here it is Port 0, in your application it may be another port.) ! Select Ethernet/IP > Cyclic frames . ! Copy the filter by clicking Copy Filter . ! Assign a new name for the filter. (Here: Cyclic frames from Slave .) 3 ! As source address, specify the MAC address of Slave 3 Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public . © Hilscher, 2008-2012 EtherNet/IP Analysis 67/128 ! Enter the identified connection ID . Caution: This connection ID must be newly determined after every network start-up ! Fill the mask fields below the MAC target address with „00“ . This prevents them from being checked. ! Fill the mask fields under the MAC source address and the connection . ID with „FF“ ! Check checkbox Select Filter . ! Select Accept, if filter A matches . ! Store the filter by clicking Save Filters . ! Select the second port under at which no telegrams have been detected (here: port 2). ! Select the filter just having been created. ! Check Select Filter . ! Check the settings for all ports. ! Leave the filter settings by clicking OK . ! Select Timing Analysis. " In the foreground, the window for the graphical display of the timing analysis opens. Figure 61: netANALYZER Timing Analysis window The timing analysis window is divided into 4 subwindows consisting of two parts, namely histogram and history. In the further discussion of this measuring set-up usually we concentrate on only one of these 4 subwindows. The size of the single subwindows can changed by dragging the point where the window division lines cross. It is also possible to display only the history window or only the histogram window. You can adjust this in the main window of the netANALYZER under Settings > Analysis Configuration. Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 EtherNet/IP Analysis 6.3.3 68/128 Settings in the Timing Analysis Windows At first, take care of Auto Scale being set. Figure 62: netANALYZER Timing-Auto-Scale In this way you ensure, that if telegrams are detected these are also visible as bars and are not outside of the window area. ! Adjust the From / To conditions for each partial window as follows: Note: At your test setup, the telegrams may run over the respective corresponding port due to the Auto-Crossover feature of the ports of the netANALYZER card. If necessary adapt the ports according to your setup! 6.3.3.1 Settings for Analysis Subwindow A Here the cycle time for telegrams from the cifX card to slave 3 shall be determined. Figure 63: EtherNet/IP Port Settings for cycle time, Timing window A ! As the telegrams from the cifX to slave 3 run over port1, you have to set From and To to „Port 1“. At you can enter a descriptive text for the measurement. Take care of the Auto Scale setting. 6.3.3.2 Settings for Analysis Subwindow B Here the propagation time of telegrams from the cifX to slave 3 through slaves 1 and 2 are measured. Figure 64: EtherNet/IP Port Settings for the propagation time from the cifX to slave 3 through slaves 1 and 2, Timing window B ! As the telegrams to slave 3 run over port 1, this port must be set under . From As the signals from slave 3 to the cifX run over Port 3 this port must be set under To Take care of the „Auto Scale“ setting at . Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 EtherNet/IP Analysis 6.3.3.3 69/128 Settings in Subwindow C Here the cycle time of input data telegrams into the Ethernet/IP network is measured. Figure 65: EtherNet/IP Port Settings for Propagation Time to Slave 3, Timing window C ! In this set-up, the telegrams of slave 3 run over port 2. For the cycle time measurement, therefore at From and To Port 2 has to be set. 6.3.3.4 Settings in Subwindow D Here the propagation time of telegrams from slave 3 to the cifX through slaves 1 and 2 is measured. Figure 66: EtherNet/IP Port Settings for the propagation time through Slave 1 and 2 to the cifX, Timing window D ! As the telegrams from slave 3 to the cifX run over Port 2 and 0 at From Port 2 and at To Port 0 has to be set. 6.3.4 Performinging the Measurements Figure 67: Main Window of netANALYZER ! Return to the main window of the netANALYZER and start a new measuring cycle by clicking Start . " You receive the following results Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 EtherNet/IP Analysis 6.3.4.1 70/128 Cycle Time for the Telegram Direction cifX to Slave 3 Figure 68: EtherNet/IP, Cycle Time for Telegram Direction cifX to Slave 3 In figure „A 1“ the histogram and in figure „A 2“ the history of the telegrams can be seen. If the From: and To: ports are identical then the cycle time is always measured, Independently of whether the direction is measured from the Master to the Slave or whether the direction is measured from the Slave to the Master. At At you can see under: Denomination Meaning Value Min Time The minimum cycle time and the percental deviation to the average cycle time 99.975 ms Av Time The average cycle time of the telegrams 100.000 m s Max Time The maximum cycle time and the percental deviation to the average propagation time 100.026 ms Std. Deviation The standard deviation of the cycle time 1.826 µs you can see under: Denomination Meaning Value Samples The number of evaluated telegrams 15618 Below Range The number of telegrams below the displayed time period (Y axis). 0 Over Range The number of telegrams above the displayed time period (Y axis). 0 Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 EtherNet/IP Analysis 6.3.4.2 71/128 Propagation Time (through Slave 1 and 2) for Telegrams cifX to Slave 3 Figure 69: EtherNet/IP, Cycle Time for Telegram Direction Slave 3 to cifX In figure „B 1“ the histogram and in figure „B 2“ the history of the telegrams can be seen. Here you can realize, that the maximum propagation time is determined by a few telegrams with very wide distance in time. Most of the telegrams pass the two slaves here with 15,397 µs. At At you can see under: Denomination Meaning Value Min Time The minimum cycle time and the percental deviation to the average cycle time 15.330 µs Av Time The average cycle time of the telegrams 15.397 µs Max Time The maximum cycle time and the percental deviation to the average propagation time 15.900 µs Std. Deviation The standard deviation of the cycle time 25 ns you can see under: Denomination Meaning Value Samples The number of evaluated telegrams 15619 Below Range The number of telegrams below the displayed time period (Y axis). 0 Over Range The number of telegrams above the displayed time period (Y axis). 0 Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 EtherNet/IP Analysis 6.3.4.3 72/128 Cycle Time Slave 3 Figure 70: EtherNet/IP, Cycle Time of Slave 3 In figure „C 1“ the histogram and in figure „C 2“ the history of the telegrams can be seen. Here, clearly two lower peaks can be identified additionally to the peak of the main cycle. These can be explained as follows. The slave has a fixed cycle time. If this time is disturbed by random events, the signal will be sent at the network a little later. This reduces the distance to the next sending by the previous time delay. Therefore, a positive and negative time delay is coupled in order to stay within the absolute cycle. At At you can see under: Denomination Meaning Value Min Time The minimum cycle time and the percental deviation to the average cycle time 99.982 ms Av Time The average cycle time of the telegrams 100.000 m s Max Time The maximum cycle time and the percental deviation to the average propagation time 100.018 ms Std. Deviation The standard deviation of the cycle time 6,830 µs you can see under: Denomination Meaning Samples The number of evaluated telegrams 15618 Below Range The number of telegrams below the displayed time period (Y axis). 0 Over Range The number of telegrams above the displayed time period (Y axis). 0 Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public Value © Hilscher, 2008-2012 EtherNet/IP Analysis 6.3.4.4 73/128 Propagation Time Slave 3 to cifX through Slave 2 and 1 Figure 71: EtherNet/IP, Propagation Time Slave 2 and 1 for Telegram Direction Slave 3 to cifX In figure „D 1“ the histogram and in figure „D 2“ the history of the telegrams can be seen. You can realize, that the propagation times of both signal directions slightly differ. You can also realize, that the maximum propagation time is caused by very few isolated events . At At you can see under: Denomination Meaning Value Min Time The minimum cycle time and the percental deviation to the average cycle time 15.234 µs Av Time The average cycle time of the telegrams 15.308 µs Max Time The maximum cycle time and the percental deviation to the average propagation time 15.824 µs Std. Deviation The standard deviation of the cycle time 26 ns you can see under: Denomination Meaning Samples The number of evaluated telegrams 15619 Below Range The number of telegrams below the displayed time period (Y axis). 0 Over Range The number of telegrams above the displayed time period (Y axis). 0 Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public Value © Hilscher, 2008-2012 EtherNet/IP Analysis 6.4 74/128 Performing Data Capture The frames of the cifX card to the Slaves and the response frames from the Slaves to the cifX card are to be captured. Preconditions: • The hardware assembly as described in section Hardware Assembly on page 56 must have been created. • The configuration for the cifX card must be accomplished (see section 6.4 of the User manual Real-Time Ethernet Kit - Communication Systems for Real-Time Ethernet Installation, Operation and Configuration). • A data exchange between the cifX card and the slaves must have been established. ! Start the netANALYZER software with Start netANALYZER > netANALYZER. " The main window of the netANALYZER opens. > Programs > Figure 72: netANALYZER Entry Screen The respective linkage status (as shown for ) is marked UP when the cabling (as described in section Hardware Assembly on page 56) has been built up and the communication between the cifX card and the NXIO board is running. ! Ensure that in the Settings > Filter Settings dialog path (as shown by ), the filter settings are set as shown in section Preparing Time Measurement on page 62. The example further below refers to the filter settings of this hardware assembly from section Hardware Assembly on page 56. Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 EtherNet/IP Analysis 75/128 ! Leave the filter settings using OK. " You are returned to the main window. Figure 73: Start Data Capture ! Ensure that Capture data is turned on. ! Start the capture with a click Start . " The Start button becomes the Stop button. ! Wait until a sufficient number of frames have been captured. ! Click Stop . . ! Click Convert " The following window appears: Figure 74: pcap Conversion 1 The pcap conversion window consists of 2 columns: Window Area User Interface Element Path Button All filtered .hea files for this name or capture Description Path to be defined by the user from which the netANALYZER shall read the binary file (*.hea) for conversion. The settings, which are done here, have an effect to the next capture. The settings done at Settings > File Settings are changed with it. Selection button for the selection of the source directory of the .hea files. List of .hea files in the selected directory. Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 EtherNet/IP Analysis 76/128 Window Area User Interface Element Description Path Path to be defined by the user where the netANALYZER software shall store the converted WinPcap file (*.pcap) Button File name .pcap files that will be generated Selection button for the selection of the target directory for storing the .pcap files Systematic file denomination for the .pcap files. The netANALYZER software additionally appends a running number for each file within the filename. Preview of generated .pcap files The name structure is as follows: File name from . consecutive number. Time information, consists of yyyymmddhhmmss (start of the capture of the hea file, if ckeck Append date/time to is set). If checked, date and time are added within the file name pcap file name Include FCS in .pcapfiles Checkbox whether the Ethernet checksum shall be included within the PCAP file or not (Some Wireshark dissectors do not support FCS.) Note: If Convert to extended .pcap file including additional frame information is checked, Include FCS in .pcap-file is grayed out as FCS is always converted into a .pcap file then. FCS = Frame Check Sequence (Ethernet checksum) Not selectable, if option Include corrupted frames in .pcap file Append netANALYZER information block (for Wireshark versions before 1.7.1 with additional plug in only) If this option is activated, then also erroneous frames will be included into the .pcap file. If it is deactivated, only correct telegrams will be stored in the .pcap file. This option requires the installation of the netANALYZER Wireshark plug-in for Wireshark versions < V1.7.1. Adds the netANALYZER info block to the .pcap file after the Ethernet frame. This supplies additional information for each single telegram such as time of receipt, receiving port or error information. Note: The .pcap file format with info block after the Ethernet frame is no longer supported by Wireshark versions ≥ 1.7.1. Not selectable if option Convert to extended .pcap file including additional frame information Convert Close is checked, however active. is checked. Note: If this item is checked, the extended .pcap file format generated by the netANALYZER software V1.4.x.x can only be opened in Wireshark versions beginning with V1.7.1. Beginning with netANALYZER software V1.4.x.x an extended .pcap file format can be generated. There the netANALYZER info block is stored in the 4 bytes prior to the Ethernet frame. Therefore, additional information for each single telegram such as time of receipt, receiving port or error information is available. Conversion of binary files into the WinPcap format is started. The window is closed without starting any conversion. . ! Select the file to be converted in window area ! Add the necessary settings in window area . ! Click Convert in order to convert the data into the .pcap file format. ! Open the file with Wireshark. " The following data will be displayed. Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 EtherNet/IP Analysis 77/128 ! Double click on the converted file (here c:\Default_001.pcap), or start the Wireshark program and select File > Open. " The Wireshark program displays the data as follows: Figure 75: EtherNet/IP netANALYZER Wireshark Telegram Display This window area shows a list of every frame which was captured at every port according to the filter. In this window area you can see individual frame regions of the selected frame. In this window area the data of the selected frame is shown at the Byte level. Here a complete frame cycle of the measurement assembly is highlighted. The first row (No 9) contains the frame as it comes from the Master. This was captured at Port 0. The second row (No 10) contains the frame after its journey through Slave 1 and Slave 2 from the Master to Slave 3. The third row (No 11) contains the frame as it returns from Slave 3 before continuing to Slave 2. The fourth row (No 12) contains the frame as it returns from Slave 3 to the Master after passing through Slaves 2 and 3. Here the part of the frame (first row of the cycle) is highlighted that contains the nominal values for the Slave. Here the part of the frame (first row of the cycle) is highlighted that contains the nominal values for the Slave 3. Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 EtherNet/IP Analysis 6.5 78/128 Preparing and Performing a Network Load Analysis The network load between slave 2 and slave 3 during start-up of the network configuration shall be determined and the load by a “ping” call shall be demonstrated. 6.5.1 Preparing Network Load Analysis As described in section Performing Data Capture on page 74, you can perform a data capture for the start-up of the network configuration to determine the relevant data for the settings, or you can use predefined filters. Here, we use the predefined filter settings. 6.5.2 Adjusting Filter Settings ! Switch off hardware filters Figure 76: Switch off Hardware Filters Note: The selected hardware filters apply additionally to the Extended at the Software Filter. Therefore uncheck either checkbox Enable Filter hardware filter or uncheck checkbox Select Filter . ! Adjust software filter. ! For the configuration of the Extended Software Filters proceed as follows: 1. In the netANALYZER main menu click at menu entry Settings > Extended Software Filter Settings. " The following configuration window is displayed: Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 EtherNet/IP Analysis 79/128 Figure 77: Extended Software Filters If the window area contains more than displayed in the figure above, then erase the entries by clicking Clear Tree . ! Click Load/Add Tree in order to select a filter. " The file manager of the operation system opens with the directory of predefined filters. ! Select the file EtherNetIP_cyclic_frame.xml . In this filter all settings for cyclic communication at an Ethernet/IP network system are already present. " After expanding all subentries, the Extended Software Filter should look like this: Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 EtherNet/IP Analysis 80/128 Figure 78: Extended Software Filters for cyclic Ethernet/IP Telegrams Additionally, the „ping“ calls at the network system shall be filtered. To do so, a further filter needs to be added to the one described above. ! Tag the entry start according to the figure above, to create an OR relation to the filter already being selected. ! Click Load/Add Tree to select a further filter. ! The file manager of the operating system opens with a the directory of the predefined filters ! Select the file ICMP_frame.xml. In this file, also the settings for a call of “ping” are contained. " The Extended Software Filter should now look like this after expanding all subentries: Figure 79: Extended Software Filters for cyclic Ethernet/IP Telegrams and Ping For each entry tagged with Identity as a new named counter is opened for the analysis, As the name Identity as Ethernet/IP cyclic frame appears four times, all these filter events will be counted into the same named counter. This also applies for the counter Identity as ICMP frame (for the „Ping“ calls) which has two sources. Note: If other data sets not matching the filter conditions appear in the telegram analysis, the counter „Other“ will automatically be added to the analysis. ! Store the filter settings for later use. By clicking OK filter window. " You return to the netANALYZER main window. Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public you leave the © Hilscher, 2008-2012 EtherNet/IP Analysis 81/128 Figure 80: netANALYZER Main Window Ethernet/IP Netload Analysis ! Check the checkbox at TAP B for Port 0 and Port 1 . This is necessary as it is not predictable over which port the communication will start due to the auto crossover feature of the Ethernet ports. ! If necessary, uncheck the checkboxes at TAP A 6.5.3 . Performing the Netload Analysis ! For performing the Netload analysis, select “Netload Analysis” in combo box . " The Netload Analysis window opens. ! In order to evaluate also the frames not originating from Ethernet/IP during connection establishment, open the Ethernet connection at CH 0 of slave 1 in Figure 52 to be able to close it again after starting the recording of the analysis. ! Select the main window of the netANALYZER. ! Here, click Start. " The recording of analysis data begins. ! Reconnect the cable at CH 0 of the slave. ! After some time, stop recording by clicking Stop in the main window of the netANALYZER. " In the Netload Analysis window you can see information similar to the following: Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 EtherNet/IP Analysis 82/128 Figure 81: Netload Analysis for Ethernet/IP Telegrams (Start-up Phase) and Ping In the figure above it can be seen, that after a network interruption at the beginning of communication some non-Ethernet/IP telegrams are recorded (Curve ) and the Ethernet/IP communication (Curve ) starts approximately 5 seconds after the end of the interruption. The „pings“ were invocated at CH 1 of slave 3 and were addressed to slave ). 1. The „ping“ call was repeated twenty times (Curve If the Ethernet/IP communication is not restarted by the network interruption, but by a power return of the slaves, the non Ethernet/IP communication will even increase in volume as in this case there is the additional communication for the address assignment via DHCP Server. This case is displayed in the next figure. Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 EtherNet/IP Analysis 83/128 Figure 82: Netload Analysis for Ethernet/IP Telegrams (Start-up Phase after Power Return) In the figure above, the non Ethernet/IP telegrams in time frame mostly result from the address assignment of the slaves over the DHCP Server and the test on identical addresses at the network. The start of the Ethernet/IP communication occurs about 16 seconds after power return. If more participants are at the network, this time will even increase. Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 SERCOS III Analysis 7 84/128 SERCOS III Analysis The following timing parameters are to be measured here as an example: • measuring the ring propagation times of the primary ring, • measuring the ConClk cycle time at Slave 1, • measuring cycle time of Master Data Telegram at the output of the master, • measuring cycle time of Master Data Telegram after passing through 3 slaves. 7.1 Hardware Assembly The following hardware assembly is required for this measurement example. Figure 83: sercos Analysis, Hardware Assembly In the example above, besides the Ethernet linkage, a 2-pole wire is to be inserted between the ConClk connection (GND Pin 1 and ConClk Pin 9) from Slave 1 to the GPIO connection 0 of the netANALYZER board. Note: The settings for the cifX card and the NXIO 50 boards must be accomplished in accordance with section 6.5 of the installation, operation and hardware description of this Kit. Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 SERCOS III Analysis 7.2 85/128 Preparing and Performing the Time Measurement Note: The cifX card and the NXIO boards offer auto crossover functionality. For this reason an interchange of the cable at the netANALYZER at TAP A (Port 0 and Port 1) as well as at TAP B (Port 2 and Port 3) is without meaning. Thus, also with the display of the analysis values of the Port designation 0/1 or 2/3 can be seen as interchangeable. Note: Only the settings of the netANALYZER immediately required for this measurement assembly are described here. Detailed information on the setting and capture possibilities of the software can be found in the User Manual netANALYZER NANL-C500-RE. 7.2.1 Preparing Time Measurement The ring propagation time of the primary ring and the ConClk cycle time at Slave 1 are to be measured. ! Start the netANALYZER software with Start > Programs > Hilscher > netANALYZER > netANALYZER. " The main window of the netANALYZER opens. Figure 84: SERCOS III netANALYZER Entry Screen The respective linkage status (as shown by ) is marked UP when the cabling (as described in section Hardware Assembly page 84) has been built up and the communication between the cifX card and the NXIO board is running then. In line you can find out, that no filter is currently active. Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 SERCOS III Analysis 7.2.2 86/128 Adjusting Filter Settings ! Select Settings > Filter Settings " The filter settings window opens. . Figure 85: SERCOS III netANALYZER SERCOS III Filter Settings For adjusting the filter settings, proceed as follows: ! Select the filter Filter > Sercos III > CP4 Frames predefined filters. ! Copy this filter by clicking Copy Filter out of the . ! Denominate the copied filter, here the name Ring ConClk is used. ! Adjust the settings according to the rectangular boxes in the illustration above! where: Multicast address , SERCOS III protocol ! Store the filter settings by clicking Save , MDT0 primary , CP4 . ! Select the filter for this port by clicking at the box Select Filter ! Click Apply to All Ports at all ports. . . in order to make this filter setting effective . ! Leave the dialog with OK " The main window of the netANALYZER opens. ! Adjust the following settings in the Settings > GPIO Settings dialog. Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 SERCOS III Analysis 87/128 Figure 86: SERCOS III netANALYZER GPIO Settings ! Set the GPIO 0 to rising edge . ! Leave the dialog with OK . " The main window of the netANALYZER opens. ! Select Timing Analysis . " The window for graphic representation of the Timing Analysis opens in the foreground: Figure 87: netANALYZER Timing Analysis window The timing analysis window is divided into 4 subwindows consisting of two parts, namely histogram and history. In the further discussion of this measuring set-up usually we concentrate on only one of these 4 subwindows. Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 SERCOS III Analysis 88/128 The size of the single subwindows can changed by dragging the point where the window division lines cross. It is also possible to display only the history window or only the histogram window. You can adjust this in the main window of the netANALYZER under Settings > Analysis Configuration. 7.2.3 Settings in the Timing Analysis Windows At first, take care of Auto Scale being set. Figure 88: netANALYZER Timing-Auto-Scale In this way you ensure, that if telegrams are detected these are also visible as bars and are not outside of the window area. ! Adjust the From / To conditions for each partial window as follows: Note: At your test setup, the telegrams may run over the respective corresponding port due to the Auto-Crossover feature of the ports of the netANALYZER card. If necessary adapt the ports according to your setup! 7.2.3.1 Settings for Analysis Subwindow A Here, the propagation time of the telegrams through the ring shall be measured. ! For a short time start the timing analysis. Under TAP A and TAP B each a port will be filled with telegrams. " The following picture resulted: Figure 89: netANALYZER Port-Selection Here it is obvious, that the telegrams at port 1 come from the cifX and return over port 2 to the cifX. ! Adjust the following settings in window A in order to measure the ringpass through time: Figure 90: Sercos Settings Timing Analysis Window A ! In this row you can enter a name for the measurement ! In From: select Port 1 . . Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 SERCOS III Analysis 89/128 ! In To: select Port 2 . With this setting the cycle time of the telegrams (selected by filter) from the master to the slave. ! Here, the scaling of the X axis (Number of telegrams) in subwindow „A 1“ (Histogram) can be switched between linear and logarithmic scaling and vice versa. ! Take care of Auto Scale being switched on. This causes the measurement result always to be displayed within the visible part of the window. 7.2.3.2 Settings for Analysis Subwindow B Measurement of ConClk cycle time at slave 1 Figure 91: Sercos Settings Timing Analysis Window B ! In From: select GPIO 0 . . ! In To: select GPIO 0 This setting is used to measure the ConClk cycle at Slave 1. ! Take care of Auto Scale 7.2.3.3 being switched on for the time scale. Settings for Analysis Subwindow C Measurement of the cycle time of the master data telegram at the output of the master. Figure 92: Sercos Settings Timing Analysis Window C ! In From: select Port 1 . ! In To: select Port 1 . Using this setting, the cycle time of the master data telegram at the output of the master is measured. ! Take care of Auto Scale being switched on for the time scale. Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 SERCOS III Analysis 7.2.3.4 90/128 Settings for Analysis Subwindow D Measurement of the cycle time of the master data telegram after passing through 3 slaves. Figure 93: Sercos Settings Timing Analysis Window D ! In From: select Port 2 . . ! In To: select Port 2 Using this setting, the cycle time of the master data telegram after passing through 3 slaves is measured. ! Take care of Auto Scale 7.2.4 being switched on for the time scale. Performing the Measurements ! Click into the main window of the netANALYZER. Figure 94: netANALYZER Start Analysis Cycle ! Click Reset ! " ! ! ! . This deletes the previously displayed time data. Click Start to start the analysis. The former Start button now becomes the Stop button. Wait as long as you want to evaluate telegrams. Wait for the time in which you would like to evaluate frames. Click Stop. Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 SERCOS III Analysis 7.2.4.1 91/128 Timing Analysis Window A: Ring Propagation Time " You will now find the following information in the window A of the Timing Analysis window: Figure 95: SERCOS III netANALYZER Ring Delay Time In figure „A 1“ (the histogram), the distribution and number of telegrams is displayed in dependence of the time. In the history window „A 2“ , the distribution of the telegrams is displayed in dependence of the time. At At you can see under: Denomination Meaning Value Min Time The minimum cycle time and the percental deviation to the average cycle time 1.764 µs Av Time The average cycle time of the telegrams 1.832 µs Max Time The maximum cycle time and the percental deviation to the average propagation time 1.894 µs Std. Deviation The standard deviation of the cycle time 20 ns you can see under: Denomination Meaning Value Samples The number of analyzed frames. 210389 Below Range The number of telegrams below the displayed time period (Y axis). 0 Over Range The number of telegrams above the displayed time period (Y axis). 0 Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 SERCOS III Analysis 7.2.4.2 92/128 Timing Analysis Window B: ConClk Cycle Time Slave 1 " You will now find the following information in the window B of the Timing Analysis window: Remark: The ConClk time depends from the cycle time adjusted at the netwerk master. The cycle time has been set to 2 ms. Figure 96: netANALYZER ConClk Cycle Time at Slave 1 In figure „B 1“ (the histogram), the distribution and number of telegrams is displayed in dependence of the time. In the history window „B 2“ , the distribution of the telegrams is displayed in dependence of the time. At At you can see under: Denomination Meaning Value Min Time The minimum cycle time and the percental deviation to the average cycle time 2.000 ms Av Time The average cycle time of the telegrams 2.000 ms Max Time The maximum cycle time and the percental deviation to the average propagation time 2.000 ms Std. Deviation The standard deviation of the cycle time 35 ns you can see under: Denomination Meaning Value Samples The number of analyzed frames. 210388 Below Range The number of telegrams below the displayed time period (Y axis). 0 Over Range The number of telegrams above the displayed time period (Y axis). 0 Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 SERCOS III Analysis 93/128 It is obvious, that there are no periodic changes of the signal within the time. 7.2.4.3 Timing Analysis Window C: Cycle Time of the Master Data Telegram at the Output of the Master Figure 97: Cycle Time Master Data Telegram Output Master In figure „C 1“ (the histogram), the distribution and number of telegrams is displayed in dependence of the time. In the history window „C 2“ , the distribution of the telegrams is displayed in dependence of the time. At you can see under: Denomination Meaning Value Min Time The minimum cycle time and the percental deviation to the average cycle time 2.000 080 ms Av Time The average cycle time of the telegrams 2.000 153ms Max Time The maximum cycle time and the percental deviation to the average propagation time 2.000 210ms Std. Deviation The standard deviation of the cycle time 22 ns The absolute jitter time amounts 130 ns. At you can see under: Denomination Meaning Value Samples The number of analyzed frames. 210388 Below Range The number of telegrams below the displayed time period (Y axis). 0 Over Range The number of telegrams above the displayed time period (Y axis). 0 Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 SERCOS III Analysis 7.2.4.4 94/128 Timing Analysis Window D: Cycle Time of the Master Data Telegram after passing through 3 Slaves One expects, that the jitter of the master data telegram is increased after passing through 3 slaves (due to their processing). Figure 98: Cycle Time Master Data Telegram after passing through 3 Slaves In figure „D 1“ (the histogram), the distribution and number of telegrams is displayed in dependence of the time. In the history window „D 2“ , the distribution of the telegrams is displayed in dependence of the time. At At you can see under: Denomination Meaning Value Min Time The minimum cycle time and the percental deviation to the average cycle time 2.000 050ms Av Time The average cycle time of the telegrams 2.000 153ms Max Time The maximum cycle time and the percental deviation to the average propagation time 2.000 290ms Std. Deviation The standard deviation of the cycle time 33 ns you can see under: Denomination Meaning Value Samples The number of analyzed frames. 210388 Below Range The number of telegrams below the displayed time period (Y axis). 0 Over Range The number of telegrams above the displayed time period (Y axis). 0 Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 SERCOS III Analysis 7.3 95/128 Performing Data Capture The frames of the cifX card to the Slaves and the response frames from the Slaves to the cifX card are to be captured. Preconditions: • The hardware assembly as described in section Hardware Assembly on page 84 must have been created, • the settings for the cifX card must be carried out, • there must be a data exchange between cifX card and the Slaves. ! Start the netANALYZER software with Start > Programs > Hilscher > netANALYZER. " The main window of the netANALYZER opens. Figure 99: SERCOS III netANALYZER Analysis Start The respective linkage status (as shown ) is marked UP when the cabling (as described in section Hardware Assembly on page 84) has been built up and the communication between the cifX card and the NXIO board is running. ! Ensure that in the Settings > Filter Settings dialog, the time settings are enabled as described in section Preparing and Performing the Time Measurement on page 85. " You are returned to the main window. Figure 100: Start Data Capture Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 SERCOS III Analysis 96/128 ! Ensure that Capture data is turned on. ! Start the capture with a click Start . " The Start button becomes the Stop button. ! Wait until a sufficient number of frames have been captured. ! Click Stop . ! Click Convert . " The following window appears: Figure 101: pcap Conversion 1 The pcap conversion window consists of 2 columns: Window Area User Interface Element Path Button All filtered .hea files for this name or capture Description Path to be defined by the user from which the netANALYZER shall read the binary file (*.hea) for conversion. The settings, which are done here, have an effect to the next capture. The settings done at Settings > File Settings are changed with it. Selection button for the selection of the source directory of the .hea files. List of .hea files in the selected directory. Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 SERCOS III Analysis 97/128 Window Area User Interface Element Description Path Path to be defined by the user where the netANALYZER software shall store the converted WinPcap file (*.pcap) Button File name .pcap files that will be generated Selection button for the selection of the target directory for storing the .pcap files Systematic file denomination for the .pcap files. The netANALYZER software additionally appends a running number for each file within the filename. Preview of generated .pcap files The name structure is as follows: File name from . consecutive number. Time information, consists of yyyymmddhhmmss (start of the capture of the hea file, if ckeck Append date/time to is set). If checked, date and time are added within the file name pcap file name Include FCS in .pcapfiles Checkbox whether the Ethernet checksum shall be included within the PCAP file or not (Some Wireshark dissectors do not support FCS.) Note: If Convert to extended .pcap file including additional frame information is checked, Include FCS in .pcap-file is grayed out as FCS is always converted into a .pcap file then. FCS = Frame Check Sequence (Ethernet checksum) Not selectable, if option Include corrupted frames in .pcap file Append netANALYZER information block (for Wireshark versions before 1.7.1 with additional plug in only) If this option is activated, then also erroneous frames will be included into the .pcap file. If it is deactivated, only correct telegrams will be stored in the .pcap file. This option requires the installation of the netANALYZER Wireshark plug-in for Wireshark versions < V1.7.1. Adds the netANALYZER info block to the .pcap file after the Ethernet frame. This supplies additional information for each single telegram such as time of receipt, receiving port or error information. Note: The .pcap file format with info block after the Ethernet frame is no longer supported by Wireshark versions ≥ 1.7.1. Not selectable if option Convert to extended .pcap file including additional frame information Convert Close is checked, however active. is checked. Note: If this item is checked, the extended .pcap file format generated by the netANALYZER software V1.4.x.x can only be opened in Wireshark versions beginning with V1.7.1. Beginning with netANALYZER software V1.4.x.x an extended .pcap file format can be generated. There the netANALYZER info block is stored in the 4 bytes prior to the Ethernet frame. Therefore, additional information for each single telegram such as time of receipt, receiving port or error information is available. Conversion of binary files into the WinPcap format is started. The window is closed without starting any conversion. ! Select the file to be converted in window area ! Add the necessary settings in window area . . ! Click Convert in order to convert the data into the .pcap file format. ! Open the file with Wireshark. " The following data will be displayed. Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 SERCOS III Analysis 98/128 " The program Wireshark displays the data as follows: Figure 102: SERCOS III netANALYZER Wireshark Telegram Display This window area shows a list of every frame which was detected according to the filter. At it can be seen at which Port of the netANALYZER the frame has arrived. Note: If in the window area the event on GPIO… is missing, then the Hilscher Wireshark Dissector has not been enabled. Enable it according to the netANALYZER user manual Rev. 8 (section 14.4). In this window area you can see individual frame area of the selected it can be seen at which Port of the netANALYZER board the frame. At frame has arrived. Caution! In order to receive the commented-upon representation (in the window area it may be necessary to download another plug-in from the SERCOS home page “https://www.sercos.org“ for the Wireshark program. In this window area the data of the selected frame is shown at the Byte level. Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 Modbus/TCP Analysis 8 99/128 Modbus/TCP Analysis The following timing parameters are to be measured here as an example: • measuring the reaction time from Slave 3, • measuring the propagation time of the frames from Slave 3 through Slaves 1 and 2, • measuring the cycle time of the cifX telegrams, • measuring the network load with Modbus/TCP telegrams at network start-up and at “ping”. 8.1 Hardware Assembly The following hardware assembly is to be carried out for this measurement example. Figure 103: Modbus/TCP Analysis, Hardware Assembly The MAC addresses applicable for the assembly are listed above the components. Ensure that the respective MAC address is unique in the world. For this reason the devices in your measurement assembly have different MAC addresses. Note: The settings for the NXIO 50 boards must be accomplished in accordance with section 6.6 of the User manual Real-Time Ethernet Kit Communication Systems for Real-Time Ethernet Installation, Operation and Configuration. Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 Modbus/TCP Analysis 100/128 Note: Ensure that the PC is not connected to the in-house network during the measurement or is uncoupled by means of a switch at the least. Otherwise incorrect measurements can occur. 8.2 Preparing and Performing the Time Measurement Note: The NXIO boards offers auto crossover functionality. For this reason an interchange of cables at the netANALYZER at TAP A (Port 0 and Port 1) as well as at TAP B (Port 2 and Port 3) has no meaning. In this way also with the display of the analysis values, the Port designations 0/1 and 2/3 can be seen as interchangeable. Note: Only the immediately required settings for this measurement assembly of the netANALYZER are described here. Detailed information on the settings and capture possibilities of the software can be found in the User Manual netANALYZER NANL-C500-RE documentation. 8.2.1 Preparing Time Measurement ! Start the netANALYZER software with Start > Program Files> Hilscher GmbH > Hilscher netANALYZER. " The main window of the netANALYZER opens. Figure 104: Modbus/TCP netANALYZER Entry Screen The respective linkage status (as shown by ) is marked UP when the cabling (as described in section Hardware Assembly on page 99) has been built up and the communication between the cifX card and the NXIO boards is running. Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 Modbus/TCP Analysis 101/128 At you can find out whether a filter is set (ACTIVE). If this is case, check whether the filter settings for the current measurement assembly are correct. Due to the auto crossover functionality of the ports at first it is necessary to examine over which ports the communication cifX > Slave 3 runs. For this purpose, certain filter settings are required. ! From the main window select Settings > Filter Settings " The filter window appears as follows. 8.2.2 . Adjusting Filter Settings 1. At first, you must determine over which ports the communication takes place into which direction. Therefore at first a filter for the telegrams from cifX to slave 3 is defined. Figure 105: Modbus/TCP netANALYZER Filter 1 ! Adjust the filter settings according to the figure above: ! Choose one port for which you want to adjust the settings. At first, this selection is not important, because in the first step the filter has to be adjusted identically for all ports. ! Select Filters > Modbus/TCP > Modbus/TCP frames . ! Copy this filter by clicking Copy Filter . ! Denominate the filter using a new name (here Modbus/TCP frames S3 ). Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 Modbus/TCP Analysis 102/128 ! Fill in the target MAC address into the area tagged in red. Here the MAC address of Slave 3 is required. ! Fill in the source MAC address in green. of the telegrams into the area tagged into the Mask fields in order to ensure comparing with ! Fill in „FF“ exactly the specified values. ! Overwrite the existing entries in both tagged areas with „00“ ! Store the filter settings by clicking Save Filter . ! Select the filter created just now for the chosen port ! Click Apply to All Ports all ports. . . in order to make the filter settings valid for ! Check whether Accept, if filter A matches is selected. ! Leave the filter settings by clicking OK . " You are returned to the main window of the netANALYZER: Figure 106: Modbus/TCP netANALYZER Filter 1 Test ! Start the timing analysis only for a short time by clicking Start and subsequently Stop (the same button). " Now you can see in the picture above that telegrams were counted in the column Frames received OK below port 1 and port 3. You can assume that these telegrams ran from the cifX (Client) to slave 3 via port 1 and port 3. Note: Due to the Auto crossover functionality of the devices, the Ports of the netANALYZER card in your measurement assembly may also run via ports 0 and 2. In this case, adapt the following settings! Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 Modbus/TCP Analysis 2. 103/128 Now, a filter for the reply of slave 3 to the cifX card needs to be created. ! Again proceed to the filter settings via Settings > Filter Settings . ! Copy the filter which you already created in order to create a new filter for the signal direction from slave 3 to client (cifX card). Proceed as follows: Figure 107: Modbus/TCP netANALYZER Filter 2 ! Select a port which did not detect any telegrams during the preceding . signal capturing. Here it is port 0 ! Select the previously defined filter Modbus/TCP frames S3 . ! Click Copy Filter in order to copy the filter. ! Denominate the copied filter using a new name, here Modbus/TCP frames S3 for the filter. ! Fill in the target MAC address of the telegrams from slave 3 to the cifX (Client) into the tagged area . ! Fill in the source MAC address of slave 3 into the tagged area ! Fill in „FF“ into the mask field the specified values. . in order to ensure exact comparison of ! Store the filter settings by clicking Save Filter . ! Select this newly stored filter for the current port (here port 0 ). ! Select the port which did not have selected any telegrams (here this is port 2 ). Click at the newly created filter in order to select it. ! Click in order to activate the filter for this port. Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 Modbus/TCP Analysis 104/128 Change to the filter Modbus/TCP frames S3. Here you select onto the telegrams with function code FC 4. Figure 108: Modbus/TCP netANALYZER Filter 3 Proceed as follows: (Line ! Fill in the value 04 for function code FC 4 at filter position 0x038, Column 0x5). Then add the mask entry „FF“ in the line below. ! Store this change by clicking Save Filter ! Leave the filter dialog by clicking OK " You are returned to the main window. Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public . . © Hilscher, 2008-2012 Modbus/TCP Analysis 105/128 Figure 109: Modbus/TCP netANALYZER Start Timing Analysis ! Select Timing Analysis . " In the foreground the window for graphic representation of the Timing Analysis opens: Figure 110: netANALYZER Timing Analysis window The timing analysis window is divided into 4 subwindows consisting of two parts, namely histogram and history. In the further discussion of this Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 Modbus/TCP Analysis 106/128 measuring set-up usually we concentrate on only one of these 4 subwindows. The size of the single subwindows can changed by dragging the point where the window division lines cross. It is also possible to display only the history window or only the histogram window. You can adjust this in the main window of the netANALYZER under Settings > Analysis Configuration. 8.2.3 Settings in the Timing Analysis Windows At first, take care of Auto Scale being set. Figure 111: netANALYZER Timing-Auto-Scale In this way you ensure, that if telegrams are detected these are also visible as bars and are not outside of the window area. ! Adjust the From / To conditions for each partial window as follows: Note: At your test setup, the telegrams may run over the respective corresponding port due to the Auto-Crossover feature of the ports of the netANALYZER card. If necessary adapt the ports according to your setup! 8.2.3.1 Settings for Analysis Subwindow A: Telegram Propagation Time Here, the telegram propagation time (of the telegrams from the cifX to slave 3) through slave 1 and 2 shall be determined. Figure 112: Modbus/TCP netANALYZER Measuring Window Settings 1 In the headline you can put in a descriptive text for the measurement . From: port of measurement (here Port 1 ), the port at which the telegrams are received from the cifX card prior to the first slave. To: port of measurement (here Port 3 ) , the port at which the telegrams arrive at the netANALYZER- card after running through slave 1 and 2. Take care of Auto Scale being switched on ensuring that the measuring results are always visible within the display window. 8.2.3.2 Settings for Analysis Subwindow B: Response Time Here the response time of slave 3 shall be measured. Figure 113: Modbus/TCP netANALYZER Start / Stop Window B In the headline you can put in a descriptive text for the measurement Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public . © Hilscher, 2008-2012 Modbus/TCP Analysis 107/128 From: port of measurement (here Port 3 telegrams arrive at slave 3. To: port of measurement (here Port 2 telegrams arrive from slave 3. ), the port at which the ), the port at which the response being switched on ensuring that the measuring Take care of Auto Scale results are always visible within the display window. 8.2.3.3 Settings for Analysis Subwindow C: Telegram Propagation Time Here, the telegram propagation time (of the telegrams from slave 3 to the cifX) through slave 1 and 2 shall be determined. Figure 114: Modbus/TCP netANALYZER Start / Stop Window C In the headline you can put in a descriptive text for the measurement From: port of measurement (here Port 2 response telegrams arrive from slave 3 . ), the port at which the ) , the port at which the response To: port of measurement (here Port 0 telegrams arrive from slave 3 after running through slave 2 and 1 Take care of Auto Scale being switched on ensuring that the measuring results are always visible within the display window. 8.2.3.4 Settings for Analysis Subwindow D: Cycle Time Here the cycle time of the telegrams from the cifX shall be measured. Figure 115: Modbus/TCP netANALYZER Start / Stop Window D In the headline you can put in a descriptive text for the measurement From: port of measurement (here Port 1 telegrams arrive from the cifX card. . ), the port at which the To: port of measurement (here Port 1 ) , the start port and stop port are identical in this case in order to be able to measure the cycle time of the telegrams. Take care of Auto Scale being switched on. This causes the measuring results always to be visible within the display window. Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 Modbus/TCP Analysis 8.2.4 108/128 Performing the Measurements ! Click the main window of the netANALYZER. Figure 116: netANALYZER main window ! Click Reset . This deletes the previously captured time data. ! Click Start to start the analysis. " The Start button becomes the Stop button. ! Wait for the time during which you would like to evaluate the frames. Note: If you want to view single partial areas during the running analysis, switch the window Auto Scale off. ! Click Stop. " In the windows you will find the following information now: 8.2.4.1 In Subwindow A: Telegram Propagation Time Here you can see the propagation time of the FC 4 telegrams to the slave (Server) 3 through slave 1 and slave 2. Figure 117: Modbus/TCP netANALYZER Analysis Window A In figure „A 1“ (the histogram), the distribution and number of telegrams is displayed in dependence of the time. In the history window „A 2“ , the distribution of the telegrams is displayed in dependence of the time. Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 Modbus/TCP Analysis 109/128 At At 8.2.4.2 you can see under: Denomination Meaning Value Min Time The minimum cycle time and the percental deviation to the average cycle time 15.918 µs Av Time The average cycle time of the telegrams 16.008 µs Max Time The maximum cycle time and the percental deviation to the average propagation time 16.098 µs Std. Deviation The standard deviation of the cycle time 31 ns you can see under: Denomination Meaning Value Samples The number of analyzed frames. 2319 Below Range The number of telegrams below the displayed time period (Y axis). 0 Over Range The number of telegrams above the displayed time period (Y axis). 0 In Subwindow B: Response Time " Here you can see the response time to the FC 4 telegrams of the cifX card to the slave (Server) 3 Figure 118: Modbus/TCP netANALYZER Analysis Window B In figure „B 1“ (the histogram), the distribution and number of telegrams is displayed in dependence of the time. In the history window „B 2“ , the distribution of the telegrams is displayed in dependence of the time. If the analysis runs over a longer time, a drift of the response time can be observed in the history window „B 2“. Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 Modbus/TCP Analysis 110/128 Figure 119: Modbus/TCP netANALYZER Analysis Window B 8.2.4.3 In Subwindow C: Response Telegram Propagation Time " You will now find the following information in sub window C of the Timing Analysis window. Figure 120: Modbus/TCP netANALYZER Analysis Window C Here you can see the propagation time of the response telegrams to the FC 4 telegrams of the cifX card to the slave (Server) 3 through slave 1 and slave 2. It is obvious to see, that there are two maxima in the distribution of the propagation time, which however are constant with regard to the time. Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 Modbus/TCP Analysis 111/128 Ahead of the measurement picture the following statistical values are displayed: At At 8.2.4.4 you can see under: Denomination Meaning Value Min Time The minimum cycle time and the percental deviation to the average cycle time 15.752 µs Av Time The average cycle time of the telegrams 15.929 µs Max Time The maximum cycle time and the percental deviation to the average propagation time 16.112 µs Std. Deviation The standard deviation of the cycle time 85 ns you can see under: Denomination Meaning Value Samples The number of analyzed frames. 5054 Below Range The number of telegrams below the displayed time period (Y axis). 0 Over Range The number of telegrams above the displayed time period (Y axis). 0 In Subwindow D: Cycle Time " You will now find the following information in sub window D of the Timing Analysis window. Figure 121: Modbus/TCP netANALYZER Analysis Window D Here you can see the cycle time with which the FC 4 telegrams of the cifX card are sent to the slave (Server) 3. In window „D 2“ it can be observed, that the distribution of the cycle time over the time is constant. Ahead of the measurement picture the following statistical values are displayed: At you can see under: Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 Modbus/TCP Analysis 112/128 At 8.3 Denomination Meaning Value Min Time The minimum cycle time and the percental deviation to the average cycle time 11.976 ms Av Time The average cycle time of the telegrams 12.000 ms Max Time The maximum cycle time and the percental deviation to the average propagation time 12.023 ms Std. Deviation The standard deviation of the cycle time 9,068 µs you can see under: Denomination Meaning Value Samples The number of analyzed frames. 2526 Below Range The number of telegrams below the displayed time period (Y axis). 0 Over Range The number of telegrams above the displayed time period (Y axis). 0 Performing Data Capture It is desired to show the frames of the PC Ethernet board to Slave 3 and the response frames from Slave 3 to the Ethernet board. Preconditions: • The hardware assembly as described in section Hardware Assembly on page 99 must be created, • the Modbus Master software must be started and linked with Slave 3. Note: At the recording of telegrams only the settings of the hardware filters are active. ! Start the netANALYZER software netANALYZER > netANALYZER. Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public with Start > Programs > © Hilscher, 2008-2012 Modbus/TCP Analysis 113/128 " The main window of the netANALYZER opens. Figure 122: Modbus/TCP netANALYZER Analysis Start The respective linkage status (as shown by ) is marked UP when the cabling (as described in section Hardware Assembly on page 99) has been built up and the communication between the cifX card and the NXIO board is running then. ! Ensure that in the Settings > Filter Settings dialog path (as shown by ), the filter settings are set as described in section Preparing Time Measurement on page 100. ! Leave the filter settings using OK. " You are returned to the main window. Figure 123: Start Data Capture ! Ensure that Capture data is turned on. ! Start the capture with a click Start . " The Start button becomes the Stop button. ! Wait until a sufficient number of frames have been captured. ! Click Stop . ! Click Convert . Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 Modbus/TCP Analysis 114/128 " The following window appears: Figure 124: pcap Conversion 1 The pcap conversion window consists of 2 columns: Window Area User Interface Element Path Button All filtered .hea files for this name or capture Description Path to be defined by the user from which the netANALYZER shall read the binary file (*.hea) for conversion. The settings, which are done here, have an effect to the next capture. The settings done at Settings > File Settings are changed with it. Selection button for the selection of the source directory of the .hea files. List of .hea files in the selected directory. Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 Modbus/TCP Analysis 115/128 Window Area User Interface Element Description Path Path to be defined by the user where the netANALYZER software shall store the converted WinPcap file (*.pcap) Button File name .pcap files that will be generated Selection button for the selection of the target directory for storing the .pcap files Systematic file denomination for the .pcap files. The netANALYZER software additionally appends a running number for each file within the filename. Preview of generated .pcap files The name structure is as follows: File name from . consecutive number. Time information, consists of yyyymmddhhmmss (start of the capture of the hea file, if ckeck Append date/time to is set). If checked, date and time are added within the file name pcap file name Include FCS in .pcapfiles Checkbox whether the Ethernet checksum shall be included within the PCAP file or not (Some Wireshark dissectors do not support FCS.) Note: If Convert to extended .pcap file including additional frame information is checked, Include FCS in .pcap-file is grayed out as FCS is always converted into a .pcap file then. FCS = Frame Check Sequence (Ethernet checksum) Not selectable, if option Include corrupted frames in .pcap file Append netANALYZER information block (for Wireshark versions before 1.7.1 with additional plug in only) If this option is activated, then also erroneous frames will be included into the .pcap file. If it is deactivated, only correct telegrams will be stored in the .pcap file. This option requires the installation of the netANALYZER Wireshark plug-in for Wireshark versions < V1.7.1. Adds the netANALYZER info block to the .pcap file after the Ethernet frame. This supplies additional information for each single telegram such as time of receipt, receiving port or error information. Note: The .pcap file format with info block after the Ethernet frame is no longer supported by Wireshark versions ≥ 1.7.1. Not selectable if option Convert to extended .pcap file including additional frame information Convert Close is checked, however active. is checked. Note: If this item is checked, the extended .pcap file format generated by the netANALYZER software V1.4.x.x can only be opened in Wireshark versions beginning with V1.7.1. Beginning with netANALYZER software V1.4.x.x an extended .pcap file format can be generated. There the netANALYZER info block is stored in the 4 bytes prior to the Ethernet frame. Therefore, additional information for each single telegram such as time of receipt, receiving port or error information is available. Conversion of binary files into the WinPcap format is started. The window is closed without starting any conversion. ! Select the file to be converted in window area ! Add the necessary settings in window area . . ! Click Convert in order to convert the data into the .pcap file format. ! Open the file with Wireshark. " The following data will be displayed. Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 Modbus/TCP Analysis 116/128 " The Wireshark program displays the data as follows: Figure 125: Modbus/TCP netANALYZER Wireshark Telegram Display This window area shows a list of all frames detected in accordance with the filter settings. Here in the Port of the netANALYZER can be found on which the frame was captured. In this window area you can see individual frame regions of the selected frame. Here, under the separate Modbus-Telegram parts can be expanded. In this window area the data of the selected frame is shown at the Byte level. A frame cycle can be seen here. The captured frames are numbered in sequence. Nr. Port Description 25 1 The point in time at which the frame (from the Master to the Slave) left the PC. 26 3 The point in time at which the frame is at the Slave 3. As the telegram contents has already been recorded, the telegram is displayed with black background and tagged with [TCP-Out-of Order]. 27 2 The point in time at which the answer frame from the Slave to the Master left the Slave 28 0 The point in time at which the answer of the Slave arrives at the PC. Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 Modbus/TCP Analysis 117/128 As recording to 2 TAPs is done and telegrams passing through may be recorded twice, Wireshark is not able to check the order of the TCP segments. Therefore the segment of a previously recorded telegram is displayed in black and marked as [TCP-Out-of Order]. Here the function code (1) in the frame has been selected and its position at the Byte level can be seen at the number . 8.4 Preparing and Perform a Network Load Analysis The network load between slave 2 and slave 3 at start-up of the network communication shall be determined and the load by a „ping“ call shall be demonstrated. 8.4.1 Preparing Network Load Analysis ! As described in section Performing Data Capture on page 112 you can perform a data capture for the network start-up to determine the relevant data for the settings, or you can use predefined settings. Here, we use the predefined filter settings. Note: During the network load analysis, always the Extended Software Filter are active. 8.4.2 Adjusting Filter Settings ! Switch off hardware filters Figure 126: Switch off Hardware Filters Note: The selected hardware filters apply additionally to the Extended at the Software Filter. Therefore uncheck either checkbox Enable Filter hardware filter or uncheck checkbox Select Filter . ! Adjust software filter. ! For the configuration of the Extended Software Filters proceed as follows: Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 Modbus/TCP Analysis 118/128 1. In the netANALYZER main menu click at menu entry Settings > Extended Software Filter Settings. " The following configuration window is displayed: Figure 127: Extended Software Filters If the window area contains more than displayed in the figure above, then erase the entries by clicking Clear Tree . in order to select a filter. ! Click Load/Add Tree " The file manager of the operation system opens with the directory of predefined filters. ! Select the file MODBUS_frame.xml . In this filter all settings for cyclic communication at an Modbus/TCP network system are already present. Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 Modbus/TCP Analysis 119/128 After expanding all subentries, the Extended Software Filter should look like this: Figure 128: Extended Software Filters for cyclic Modbus/TCP Telegrams Additionally, the „ping“ calls at the network system shall be filtered. To do so, a further filter needs to be added to the one described above. ! Tag the entry Start according to the figure above to create an OR relation to the filter already being selected. ! Click Load/Add Tree to select a further filter. ! The file manager of the operating system opens with a the directory of the predefined filters ! Select the file ICMP_frame.xml. In this file, also the settings for a call of “ping” are contained. Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 Modbus/TCP Analysis 120/128 ! The Extended Software Filter should now look like this after expanding all subentries: Figure 129: Extended Software Filters for cyclic MODBUS/TCP Telegrams and Ping For each entry tagged with Identity as a new named counter is opened for the analysis, As the name Identity as MODBUS/TCP frame appears four times, all these filter events will be counted into the same named counter. This also applies for the counter Identity as ICMP frame (for the „Ping“ call) which has two sources. Note: If other data sets not matching the filter conditions appear at the telegram analysis, the counter Other will automatically be added to the analysis. ! Store the filter settings for later use. By clicking OK filter window. " You return to the netANALYZER main window. Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public you leave the © Hilscher, 2008-2012 Modbus/TCP Analysis 121/128 Figure 130: netANALYZER Main Window MODBUS/TCP Netload Analysis ! Check the checkbox at TAP B for Port 0 and Port 1 . This is necessary as it is not predictable over which port the communication will start due to the auto crossover feature of the Ethernet ports. ! If necessary, uncheck the checkboxes at TAP A 8.4.3 . Performing the Network Load Measurement ! For performing the Netload analysis, select Netload Analysis in combo . box " The Netload Analysis window opens ! In order to evaluate also the frames not originating from Modbus/IP during connection establishment, open the Ethernet connection at CH 0 of slave 1 in Figure 103 to be able to close it again after starting the recording of the analysis. ! Select the main window of the netANALYZER. ! Here, click Start. " The recording of analysis data begins. ! Reconnect the cable at CH 0 of the slave. ! After some time, stop recording by clicking Stop in the main window of the netANALYZER. " In the Netload Analysis window you can see information similar to the following: Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 Modbus/TCP Analysis 122/128 Figure 131: Network Load for cyclic MODBUS/TCP Telegrams and Ping In the figure above it can be seen, that after a network interruption at the beginning of communication some non-MODBUS/TCP telegrams are recorded (Curve ) and the MODBUS/TCP communication (Curve ) starts approximately 1 second after the end of the interruption. The „pings“ were invocated at CH 1 of slave 3 and were addressed to slave ). The first “ping” 1. The „ping“ call was repeated twenty times (Curve call is started with an ARP telegram. Thus, there is a peak at telegram counter Other. If the Modbus/TCP communication is not restarted by the network interruption, but by a power return of the slaves, the non Modbus/TCP communication will even increase in volume as in this case there is the additional communication for the address assignment via DHCP Server. This case is displayed in the next figure. Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 Modbus/TCP Analysis 123/128 Figure 132: Netload Analysis for Modbus/TCP Telegrams (Start-up Phase after Power Return) In the figure above, the non Modbus/TCP telegrams in time frame mostly result from the address assignment of the slaves over the DHCP Server and the test on identical addresses at the network. The start of the cyclic Modbus/TCP communication occurs about 13 seconds after power return. If more participants are at the network, this time will even increase. , If you follow with the mouse pointer along a measurement line in figure the mouse pointer will change to a hand and the number of telegrams counted per second for this filter is displayed. Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 Glossary 9 124/128 Glossary CSV Comma Separated Value GPIO General Purpose Input/Output hea File ending of the generated binary file (default.hea) of the Hilscher netANALYZER software with the Capture Information content. .NET Framework Version 2.0 Microsoft .NET Framework Version 2.0 http://www.microsoft.com/downloads/details.aspx?familyid=0856EACB-43624B0D-8EDD-AAB15C5E04F5&displaylang=de PIO Programmable Input/Output TAP Test Access Point Wireshark “Wireshark Network monitoring program” http://www.wireshark.org WinPcap “The WinPcap” library” http://www.winpcap.org/ Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 Appendix 125/128 10 Appendix 10.1 List of Figures Figure 1: netANALYZER Main Window Figure 2: netANALYZER File Settings Figure 3: Timing analysis, change scaling Figure 4: Timing Analysis, scaling with the Mouse Figure 5: PROFINET IO Analysis, Hardware Assembly Figure 6: netANALYZER Entry Screen Figure 7: netANALYZER Filter Settings (1) Figure 8: netANALYZER Filter Settings (2) Figure 9: netANALYZER, Selection Timing Analysis Figure 10: netANALYZER Measurement Window Figure 11: netANALYZER Main Window after Measurement Cycle Figure 12: netANALYZER Measurement Window Settings 1 Figure 13: netANALYZER Measuring Window Settings 2 Figure 14: netANALYZER Main Window Start/Reset Figure 15: netANALYZER PROFINET IO Cycle time Measurement, auto-scale Figure 16: PROFINET IO, Device 1 Propagation time Figure 17: PROFINET IO, Device 1 Propagation Time, History extremely scaled Figure 18: Main Window for Telegram Recording Figure 19: netANALYZER PROFINET IO Filter Settings Figure 20: Start Data Capture Figure 21: pcap Conversion 1 Figure 22: PROFINET IO netANALYZER Wireshark Telegram Display Figure 23. Standard PROFINET Data Set Figure 24: Switch off hardware filter Figure 25: Create Extended Software Filter (1) Figure 26: Create Extended Software Filter (2) Figure 27: Extended Software Filter after 1. Entry Figure 28: Extended Software Filter after 2. Entry Figure 29. Extended Software Filter after 3. Entry Figure 30: netANALYZER Main Window PROFINET Netload Analysis Figure 31: Netload Analysis for PROFINET Start-up Phase Figure 32: Extended Software Filter with FrameID Figure 33: Netload Analysis for PROFINET Start-up Phase with FrameID 8002 Figure 34: EtherCAT Analysis, Hardware Assembly Figure 35: netANALYZER Entry Screen Figure 36: netANALYZER Filter Window Figure 37: netANALYZER Timing Analysis window Figure 38: netANALYZER Timing-Auto-Scale Figure 39: Timing Analysis Window A, EtherCAT Cycle Time Figure 40: Timing Analysis Window B, EtherCAT Ring Propagation Time (1) Figure 41: Timing Analysis Window C, EtherCAT Ring Propagation Time (2) Figure 42: Timing Analysis Window, EtherCAT Ring Propagation Time (2) Figure 43: netANALYZER Start/Stop Analysis Figure 44: EtherCAT Timing Analysis Window A with measured Data Figure 45: EtherCAT Timing Analysis Window B with measured Data Figure 46: EtherCAT Timing Analysis Window C with measured Data Figure 47: EtherCAT Timing Analysis Window D with measured Data Figure 48: EtherCAT netANALYZER Main Window Figure 49: Start Data Capture Figure 50: pcap Conversion 1 Figure 51: EtherCAT netANALYZER Wireshark Telegram Display Figure 52: EtherNet/IP Analysis, Hardware Assembly Figure 53: EtherNet/IP Filter Data Capture Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public 12 13 14 15 16 17 18 19 21 22 23 24 24 25 25 26 27 28 29 29 30 32 33 34 34 35 35 36 37 38 39 40 40 41 42 43 44 44 45 45 45 46 46 47 48 50 51 52 53 53 55 56 57 © Hilscher, 2008-2012 Appendix 126/128 Figure 54: EtherNet/IP Data Capture Start 58 Figure 55: Ethernet/IP netANALYZER Analysis Conversion 1 59 Figure 56: EtherNet/IP Data Capture 61 Figure 57: EtherNet/IP netANALYZER Entry Screen 63 Figure 58: EtherNet/IP netANALYZER Filter cifX # Slave 3 64 Figure 59: EtherNet/IP netANALYZER Direction of Signal Flow 65 Figure 60: EtherNet/IP netANALYZER Filter Slave 3 # cifX 66 Figure 61: netANALYZER Timing Analysis window 67 Figure 62: netANALYZER Timing-Auto-Scale 68 Figure 63: EtherNet/IP Port Settings for cycle time, Timing window A 68 Figure 64: EtherNet/IP Port Settings for the propagation time from the cifX to slave 3 through slaves 1 and 2, 68 Timing window B Figure 65: EtherNet/IP Port Settings for Propagation Time to Slave 3, Timing window C 69 Figure 66: EtherNet/IP Port Settings for the propagation time through Slave 1 and 2 to the cifX, Timing 69 window D Figure 67: Main Window of netANALYZER 69 Figure 68: EtherNet/IP, Cycle Time for Telegram Direction cifX to Slave 3 70 Figure 69: EtherNet/IP, Cycle Time for Telegram Direction Slave 3 to cifX 71 Figure 70: EtherNet/IP, Cycle Time of Slave 3 72 Figure 71: EtherNet/IP, Propagation Time Slave 2 and 1 for Telegram Direction Slave 3 to cifX 73 Figure 72: netANALYZER Entry Screen 74 Figure 73: Start Data Capture 75 Figure 74: pcap Conversion 1 75 Figure 75: EtherNet/IP netANALYZER Wireshark Telegram Display 77 Figure 76: Switch off Hardware Filters 78 Figure 77: Extended Software Filters 79 Figure 78: Extended Software Filters for cyclic Ethernet/IP Telegrams 80 Figure 79: Extended Software Filters for cyclic Ethernet/IP Telegrams and Ping 80 Figure 80: netANALYZER Main Window Ethernet/IP Netload Analysis 81 Figure 81: Netload Analysis for Ethernet/IP Telegrams (Start-up Phase) and Ping 82 Figure 82: Netload Analysis for Ethernet/IP Telegrams (Start-up Phase after Power Return) 83 Figure 83: sercos Analysis, Hardware Assembly 84 Figure 84: SERCOS III netANALYZER Entry Screen 85 Figure 85: SERCOS III netANALYZER SERCOS III Filter Settings 86 Figure 86: SERCOS III netANALYZER GPIO Settings 87 Figure 87: netANALYZER Timing Analysis window 87 Figure 88: netANALYZER Timing-Auto-Scale 88 Figure 89: netANALYZER Port-Selection 88 Figure 90: Sercos Settings Timing Analysis Window A 88 Figure 91: Sercos Settings Timing Analysis Window B 89 Figure 92: Sercos Settings Timing Analysis Window C 89 Figure 93: Sercos Settings Timing Analysis Window D 90 Figure 94: netANALYZER Start Analysis Cycle 90 Figure 95: SERCOS III netANALYZER Ring Delay Time 91 Figure 96: netANALYZER ConClk Cycle Time at Slave 1 92 Figure 97: Cycle Time Master Data Telegram Output Master 93 Figure 98: Cycle Time Master Data Telegram after passing through 3 Slaves 94 Figure 99: SERCOS III netANALYZER Analysis Start 95 Figure 100: Start Data Capture 95 Figure 101: pcap Conversion 1 96 Figure 102: SERCOS III netANALYZER Wireshark Telegram Display 98 Figure 103: Modbus/TCP Analysis, Hardware Assembly 99 Figure 104: Modbus/TCP netANALYZER Entry Screen 100 Figure 105: Modbus/TCP netANALYZER Filter 1 101 Figure 106: Modbus/TCP netANALYZER Filter 1 Test 102 Figure 107: Modbus/TCP netANALYZER Filter 2 103 Figure 108: Modbus/TCP netANALYZER Filter 3 104 Figure 109: Modbus/TCP netANALYZER Start Timing Analysis 105 Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012 Appendix 127/128 Figure 110: netANALYZER Timing Analysis window Figure 111: netANALYZER Timing-Auto-Scale Figure 112: Modbus/TCP netANALYZER Measuring Window Settings 1 Figure 113: Modbus/TCP netANALYZER Start / Stop Window B Figure 114: Modbus/TCP netANALYZER Start / Stop Window C Figure 115: Modbus/TCP netANALYZER Start / Stop Window D Figure 116: netANALYZER main window Figure 117: Modbus/TCP netANALYZER Analysis Window A Figure 118: Modbus/TCP netANALYZER Analysis Window B Figure 119: Modbus/TCP netANALYZER Analysis Window B Figure 120: Modbus/TCP netANALYZER Analysis Window C Figure 121: Modbus/TCP netANALYZER Analysis Window D Figure 122: Modbus/TCP netANALYZER Analysis Start Figure 123: Start Data Capture Figure 124: pcap Conversion 1 Figure 125: Modbus/TCP netANALYZER Wireshark Telegram Display Figure 126: Switch off Hardware Filters Figure 127: Extended Software Filters Figure 128: Extended Software Filters for cyclic Modbus/TCP Telegrams Figure 129: Extended Software Filters for cyclic MODBUS/TCP Telegrams and Ping Figure 130: netANALYZER Main Window MODBUS/TCP Netload Analysis Figure 131: Network Load for cyclic MODBUS/TCP Telegrams and Ping Figure 132: Netload Analysis for Modbus/TCP Telegrams (Start-up Phase after Power Return) 105 106 106 106 107 107 108 108 109 110 110 111 113 113 114 116 117 118 119 120 121 122 123 10.2 List of Tables Table 1: List of Revisions Table 2: Overview of Measuring Examples Table 3: Description File Settings Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public 4 10 13 © Hilscher, 2008-2012 Appendix 128/128 10.3 Contacts Headquarters Germany Hilscher Gesellschaft für Systemautomation mbH Rheinstrasse 15 65795 Hattersheim Phone: +49 (0) 6190 9907-0 Fax: +49 (0) 6190 9907-50 E-Mail: [email protected] Support Phone: +49 (0) 6190 9907-99 E-Mail: [email protected] Subsidiaries China Japan Hilscher Systemautomation (Shanghai) Co. Ltd. 200010 Shanghai Phone: +86 (0) 21-6355-5161 E-Mail: [email protected] Hilscher Japan KK Tokyo, 160-0022 Phone: +81 (0) 3-5362-0521 E-Mail: [email protected] Support Support Phone: +86 (0) 21-6355-5161 E-Mail: [email protected] Phone: +81 (0) 3-5362-0521 E-Mail: [email protected] France Korea Hilscher France S.a.r.l. 69500 Bron Phone: +33 (0) 4 72 37 98 40 E-Mail: [email protected] Hilscher Korea Inc. Suwon, Gyeonggi, 443-734 Phone: +82 (0) 31-695-5515 E-Mail: [email protected] Support Phone: +33 (0) 4 72 37 98 40 E-Mail: [email protected] India Hilscher India Pvt. Ltd. New Delhi - 110 065 Phone: +91 11 43055431 E-Mail: [email protected] Switzerland Hilscher Swiss GmbH 4500 Solothurn Phone: +41 (0) 32 623 6633 E-Mail: [email protected] Support Phone: +49 (0) 6190 9907-99 E-Mail: [email protected] Italy USA Hilscher Italia S.r.l. 20090 Vimodrone (MI) Phone: +39 02 25007068 E-Mail: [email protected] Hilscher North America, Inc. Lisle, IL 60532 Phone: +1 630-505-5301 E-Mail: [email protected] Support Support Phone: +39 02 25007068 E-Mail: [email protected] Phone: +1 630-505-5301 E-Mail: [email protected] Real-Time Ethernet Kit | Analysis Examples DOC081202UM04EN | Revision 4 | English | 2012-11 | Released | Public © Hilscher, 2008-2012