Download Layer 2 Managed Stackable Switches
Transcript
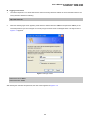
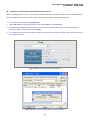
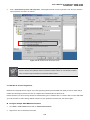
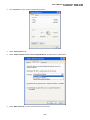
User’s Manual of SGSD-1022 / SGSD-1022P SGSW-2840 / SGSW-2840P 4.11.13 Access Control Lists Access Control Lists (ACL) provide packet filtering for IP frames (based on address, protocol, Layer 4 protocol port number or TCP control code) or any frames (based on MAC address or Ethernet type). To filter incoming packets, first create an access list, add the required rules, and then bind the list to a specific port. Configuring Access Control Lists – An ACL is a sequential list of permit or deny conditions that apply to IP addresses, MAC addresses, or other more specific criteria. This switch tests ingress or egress packets against the conditions in an ACL one by one. A packet will be accepted as soon as it matches a permit rule, or dropped as soon as it matches a deny rule. If no rules match for a list of all permit rules, the packet is dropped; and if no rules match for a list of all deny rules, the packet is accepted. The following filtering modes are supported: • Standard IP ACL mode (STD-ACL) filters packets based on the source IP address. • Extended IP ACL mode (EXT-ACL) filters packets based on source or destination IP address, as well as protocol type and protocol port number. If the TCP protocol is specified, packets can also be filtered based on the TCP control code. • MAC ACL mode (MAC-ACL) filters packets based on the source or destination MAC address and the Ethernet frame type (RFC 1060). Command Usage The following restrictions apply to ACLs: • The maximum number of ACLs is 32. • Each ACL can have up to 100 rules. However, due to resource restrictions, the average number of rules bound to the ports should not exceed 20. The order in which active ACLs are checked is as follows: • User-defined rules in the Egress IP ACL for egress ports. • User-defined rules in the Ingress IP ACL for ingress ports. • Explicit default rule (permit any any) in the ingress IP ACL for ingress ports. • If no explicit rule is matched, the implicit default is permit all. 4.11.13.1 ACL Configuration Use the ACL Configuration page to designate the name and type of an ACL. 311
Related documents

JetNet 5228G User Manual V1.1

Edge-Core ES3526XA V2 EU

Edge-Core ES3528M-SFP

Planex SF-2420GX System information

TigerSwitch 10/100 Management Guide

User manual - Edge-Core

LevelOne KIT:FGL-2870 + 4 x GVT-0300

Edge-Core ES3528MV2-DC System information

SignaMax F0-065-1200 Series Installation manual

Edge-Core ES4524M-PoE EU

User`s Manual of Layer 2 Management 802.3at PoE Switch

Planet Technology SGSW-2402 User's Manual

Sun Fire X4170 M2 and X4270 M2 Servers Installation Guide

EnGenius L2 Switch CLI Manual

TigerSwitch 10G

Product Specification

Product Specification

Product Specification

User`s Manual - PLANET Technology Corporation.

Thermador Cooktop SGSL User's Manual

TigerSwitch 10/100 Management Guide

GSW-2404SF User Manual