Download Red Hat NETSCAPE ENTERPRISE SERVER 6.0 - NSAPI PROGRAMMER GUIDE User guide
Transcript
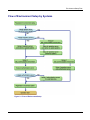
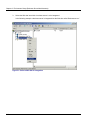
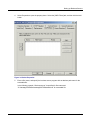
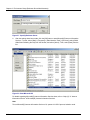
Chapter 7: Developing Applications Table 7-15 Setting Access Permissions for Files (Windows) Resource Explanation Service ID file Set access permission when a Java application that receives a user ID/password from a client to perform authentication is not to use the business server configuration. Permit only a Java application execution user (or IJServer user for a servlet application) to read the file. Login configuration file Permit only a Java application execution user (or IJServer user for a servlet application) to read the file. Security policy file Permit only a Java application execution user to read the file. Trust store file Set access permission when a Java application that receives a user ID/password from a client to perform authentication is to be used. - When a file is created using the Interstage certificate environment Permit a Java application execution user (or IJServer user for a servlet application) to read the file. - When a file is created using a keytool command Permit only a Java application execution user (or IJServer user for a servlet application) to read the file. Use a chmod or chown command. Set access permission with super user (root) authority. Table 7-16 Setting Access Permissions for Files (Solaris and Linux) Resource Explanation Service ID file Set access permission when a Java application that receives a user ID/password from a client to perform authentication is not to use the business server configuration. Permit only a Java application execution user (or IJServer user for a servlet application) to read the file. Login configuration file Permit only a Java application execution user (or IJServer user for a servlet application) to read the file. Security policy file Permit only a Java application execution user to read the file. Trust store file Set access permission when a Java application that receives a user ID/password from a client for authentication is to be used: - When a file is created using the Interstage certificate environment Permit a Java application execution user (or IJServer user for a servlet application) to read the file. - When a file is created using a keytool command Permit only a Java application execution user (or IJServer user for a servlet application) to read the file. 7-30