Download Troubleshooting WLAN
Transcript
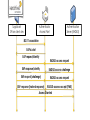
Troubleshooting WLANs Tips and tricks with practical examples ! ! by Gregor Vucajnk, Knowledge Services at Aerohive Networks email: gvucajnk(at)aerohive.com, twitter: @GregorVucajnk Get a free Aerohive AP/management General International/Freeval AP webinar page:! http://www.aerohive.com/news-events/international-webinars ! Registration page of the event held in Dutch language:! http://info.aerohive.com/June-simplified-wireless-Registration-LandingPage-NL.html “Troubleshooting is more of an art form than exact science.” – The Internet AGENDA • Troubleshooting strategy. • Basic troubleshooting methodology. • Practical examples with commentary. 1. TROUBLESHOOTING STRATEGY Dilbert 40 years of age IT generalist Babysits the rest of the IT team (usually junior members) Source: www.dilbert.com 3. Basic Troubleshooting methodology • Identifying the issue • Recreate problem • Locate and isolate the cause • Formulate a plan of solving the problem • Implement the plan • Test to very the problem is resolved • Document the problem and the solution • Provide feedback to user RINSE AND REPEAT 3. Practical examples 802.11 passive discovery • • Client devices can learn about the networks from listening to the n e beacon frames. Beacon frames are sent rfrom the AP, advertising it h W . : n o o i f t y l l a k a i m o t r o n o l f e n s o services. It contains the information about the SSID and capabilities but i t s t t e n a a d t r n s o a i Wh p ) e r 1 m i u 1 t l 5 p a 0 r a also serves other purposes (like time sync between all STA in SS, x e c 0 v ( e e n h s t o i y , t r r . r a e g a b m n c i r m v o s i f e e e n i m indication of buffered data for devices in sleep mode, etc). c m e e s r a r e d t i f t u e li i n B b o b . c n a s a r a p e e a C t B . e C e m g c i a n i r v t a e o p d o h g g s a n i e T l r r u b t e u p d o r a By default the AP will send the beacon frame every* 100 TU (102.4ms), n t c u e s h g t a f T o e n h o t i t l l a a to network t subject congestion. e r p r e t n i an 802.11 beacon frames (wlan.fc.type_subtype eq 8) e h t 802.11 active discovery s n ! i a : t r t n u o f o o c b t a I . o look e nf • • o i m t l a t r a f a n t h o s i t o i a W s c d l d a d Client devices can learn about the b networks by actively sending probe requests a t a s o r n e i u a t q a n e o y r l l c e a e y b u c i a o s (broadcast if SSID is unknown or directed if searching for specific SSID). APs that r v u m e P s . d o i ) s t l e c t s a h t e e d , u s r n q a e a r e r r u e u t hear the probe request will answer with unicast probe response. The information e c o c . i i b s a v v f o n e a u o d h i Pr n t e a e c b h e m t n g , f n n e o i o d in probe response is very similar to content of a beacon frame minus TIM field, s m c o e a r i t m o i e l r i h e t b e c o i a c i v r p v e o a f e d c ( d s g i t e QoS capability IE. Probe response can however include other information if n t i n I c k i e . i v o l e e o r c l d u t d e e c n m h u e i t r t t n i n s e o d h explicitly requested with RIEs (request information element) in probe request. n l t t i e l o l l e fi a ! a m s M l a s I r e y T f n a o n s n n o a c h s i a c e n e s r o b i p e t o h a t t ho T r s . a l a e i t t a m a i r Timing of the probe request sent is dependent on the client device and OS s h t n y t o r n e m e v m m s o i e l c e e t s s E n I e implementation. o R w p o s n l i t e s a r e t e h n e t u o t b q c a o e r r t y P n a e e b m s o t r i d t p n u a e b t h t s e a s a i c n i v o n d p u e s t e s r e e u b q (wlan.fc.type_subtype eq 4) e pro802.11 proberrequest 802.11 probe response (wlan.fc.type_subtype eq 5) 802.11 authentication • 802.11 authentication should not be confused with network e h authentication. It is a simple two frame sexchange in between the end t r ! e : v e e w k o a r H . b d k t e r i t o n client device and the AP.W Inhsimple terms, it is the end client device e w ere s m y e l a p w l m i a s d i l u g o n i saying to the AP "I can see you" and the AP is replying "I can see h r s e t l n fi o i t C a A c . i l t M e n f v i e l n you too”. 2.11 authe e broken o i t a r u g b fi 80 n n a o c c e D I g S n S a at a exch 802.11 authentication request (wlan.fc.type_subtype eq 11) 802.11 authentication response (wlan.fc.type_subtype eq 11) k r 802.11 association o w ! t : e r n o r f o e f k h t o s t lo en (or o t m d t e e r a i d h u y a q a o W l e r r m e e v P h o A t s e i p h u t P • 802.11 association is forsethe , client device to joining the SS and s A ) g t f s n I i n r . ) o e i e t X e s t a 1 i a . s c h 2 d o 0 p s n 8 n s a , o a b i K t f obtain the AID (Association ID). Association exchange sets and S a o m i P t o c r P n o f , u s t o s K c S A a m P p a . ( w m e i n o h o t fl i n t t l a i l synchronizes dependencies and requirements for joining the SS. a a c o m i i c l t s l n e a o t e h s t t h i t t e u e c s r a e e s f i f h a e n T r o . n a i Association frames are unicast. The Association request frame t s a s a n c r e o t t i u t a a g r a h i fi t ) c n y g o r o . s n y o c i t t s i c a a c n d t a a l n n p contains the capabilities of the device and the association response a a e a ! i l b c m c ( k d t r c a c i o o e s l j e w a t e h d t r e b n t n r e a l l o h t a p r , frame provides with requirements to join the SS p e e u v s s o a t h e o p h n t n y n o a i o t t m a i c c e a o c i p s v s m e i a . d t S e t c S h n e t r i e e i l n d h t c o a o d d t s n e a s g e h n i e t s Ba i h a t i h , c T y l o . e s d v s i e t a 802.11 association request (wlan.fc.type_subtype eq 0) s a s i s l t e i r o a f g g e g d n a n a o t s d e t e a k r a c e i s w 802.11 association response (wlan.fc.type_subtype eq 1) t a b If e 802.11 active discovery h t s n ! i a : t r t n u o f o o c . It ook o ab • • l f e n o i m t l a t r a f a n t h o s i t o i a W thernetworks s Client devices can learn about by actively sending probe requests c d l d a d a t a s o n e i b u a t q a n e o y r l l c e a e y (broadcast if SSID isisunknown or directed if searching for specific SSID). APs that b u c i a o s r v u m e P . d o ) s t l e c t s a h t e e d , u s r n q a e a r e requestvwill hear theobprobe answer with unicast probe response. The information r r u e u t e c o c . i i s a v f n e a r u o d h i P n t e a e c b h e m t n g , f n in probeitresponse is very similar to content of a beacon frame minus TIM field, n e o i o d s m c o e a r i m o e l r i h e t b e c o i a c i v r p v e o a f e d c capability ( QoS IE. Probe response can however include other information if d s g i t e n t i n I c k i e . i v o l e e o r c l d u t d e e c n m h u e i t r t t n i n explicitly requested with RIEs (request information element) in probe request. s e o d h n l t t i e l o l l e fi a ! a m s M l a s I r e y T f n a o n s n n o a c h s i a c e n e s r o b i p e t o o h a t t h T r s . a l a e i t t Timing of the probe request rsent is dependent on the client device and OS a m a i r s h t n y t o n e m e v m m s o i e l c e e t s implementation. s E n I e o R w p o s n l i t e s a r e t e h n e t u o t b q c a o e r r t y P n a e e b m s o t r i d t p n u a e b t h t s e a s a i c n i v o n d p u e s t e s r e e u 802.11 probe request (wlan.fc.type_subtype eq 4) b q o e r r p 802.11 probe response (wlan.fc.type_subtype eq 5) Additional management frames • Reassociation request (wlan.fc.type_subtype eq 2) already a part of ESS and roaming to new AP • Reassociation reponse (wlan.fc.type_subtype eq 3) similar to association but when roaming within ESS • Diassociation (wlan.fc.type_subtype eq 10) (used in roaming to terminate connection) • Deauthentication (wlan.fc.type_subtype eq 12) sent when all communication is terminated, ie, when the AP is rebooting). 4-way handshake • Process by the source key material is turned in encryption material to encrypt our communication. • It is done for EVERY* WPA(2) association and reasocciation (there is a slight difference when using 802.11r). • Directly follows association phase for WPA(2)-Personal. • Follows full EAP authentication for WPA(2)-Enterprise. • Consists of four unicast frames. • Only upon successfully completing the 4-way handshake is the traffic from the client device allowed to the network past the AP. PMK is known Generate SNonce PMK is known Generate ANonce Message 1: EAPOL-Key (ANonce) Derive PTK Message 2: EAPOL-Key (Snonce, MIC) Derive PTK Generate GTK Message 3: EAPOL-Key (Install PTK, MIC, Encrypted GTK) Message 4: EAPOL-Key (MIC) Install PTK and GTK Install PTK and GTK 4-way handshake l e v e l r e h g i • After Message1 (1/4 is sent) -> Driver issue. Reboot, h update driver. y n t a a e s t i a r y t i e v b i t u c x e e n n n a o c c y 1 t i L v i t e r c u e s • After Message2 (2/4co n is sent) -> Wrong PSK, wrong time with PPSK. n e k a F M . . R s s l d e e a u v s b e l s : i t e l n b o i a Hin t t a p c i e n c u c a m m • After Message co 3 (3/4 is sent) -> Driver issue. Reboot, update driver. • After Message 4 (4/4 is sent) -> It becomes a network issue. Check DHCP, DNS, FW, VLANs, etc. Supplicant SW on client dev Authenticator Access Point Authentication Server (RADIUS) 802.11 association EAPoL-start EAP-request/identity RADIUS-access-request EAP-response/identity RADIUS-access-challenge EAP-request (challenge) RADIUS-access-request EAP-response (hashed response) RADIUS-access-accept (PMK) Access Granted Closing thoughts • Time is money! • Be conservative. • Create a lab and break everything. www.aerohive.com